📜 Introduction — Why This Guide Exists
The internet, as it was originally designed, had no concept of privacy, security, or scale. It was a small academic experiment, never intended for billions of users or the commercial world. As the internet expanded rapidly in the 1990s and 2000s, several critical problems emerged:
- A severe shortage of IP addresses.
- No built-in protection from attackers.
- No privacy or encryption.
- No control over who connects to what.
To patch these problems, networking engineers developed technologies like NAT, Proxy, VPN, and Firewalls — essential tools that became the foundation of modern network security. Each of these tools addresses a specific weakness in the internet’s design.
⚠️ Disclaimer
This article is written for educational and ethical purposes only. Its goal is to help readers understand how NAT, proxies, VPNs, and firewalls work to improve security, privacy, and cybersecurity awareness. The information provided is not intended for illegal use.
🛰️ Part 1 — NAT (Network Address Translation)
📖 The Origin of NAT
In the late 1980s and early 1990s, it became clear that the world was running out of IPv4 addresses — a problem now known as IPv4 exhaustion. IPv4, created in the 1980s, only supports 4.3 billion IP addresses, which quickly became insufficient as personal computers, mobile devices, and enterprise networks multiplied.
In 1994, the IETF published RFC 1631, introducing NAT as a temporary workaround. NAT became one of the most successful “temporary” solutions in internet history.
🔧 How NAT Works
🔀 NAT Traversal (ASCII Diagram): How Two Clients Communicate Through NAT
pgsql+-----------+ +-------------+ +-------------+ +-----------+
| Client A |<-------->| NAT Router A|<------->| Internet |<------->| STUN Server|
+-----------+ +-------------+ +-------------+ +-----------+
|
| STUN request
v
[Public IP:Port of A]
|
|--------------------------+
|
| STUN shares A’s public IP with B
|
|<-------------------------|
+-----------+ +-------------+
| Client B |<-------->| NAT Router B|
+-----------+ +-------------+
|
| STUN request → [Public IP:Port of B]
|
| Both clients now know each other's public IPs
|
| <------------ Direct P2P connection ------------>
💡 Explanation
- Client A and Client B are both behind NAT routers.
- Each sends a request to the STUN server to discover its own public IP and port.
- The STUN server shares this information between them.
- The clients now attempt a direct peer-to-peer (P2P) connection using their public endpoints.
- This method works best with cone NATs and compatible routers.
NAT allows multiple devices on a private network to share a single public IP address. The router keeps track of connections using a NAT translation table, which maps private IP addresses and ports to public ports.
| Internal IP | Internal Port | Public IP | Public Port | Protocol |
|---|---|---|---|---|
| 192.168.0.5 | 43215 | 203.0.113.5 | 55789 | TCP |
When the router receives responses from the internet, it uses the table to forward them to the correct device on the internal network.
⚙️ Types of NAT
- Static NAT: One-to-one mapping between private and public IPs.
- Dynamic NAT: Maps private IPs to a pool of public IPs.
- PAT (Port Address Translation): Maps multiple devices to one public IP using different ports (the most common).
⚠️ NAT Traversal Problem
NAT works perfectly for outbound connections but blocks unsolicited inbound connections. This creates issues for peer-to-peer apps, VoIP, and gaming.
To solve this, technologies like STUN, TURN, and ICE were developed, allowing devices behind NAT to establish connections.
🗺️ NAT Traversal Diagram
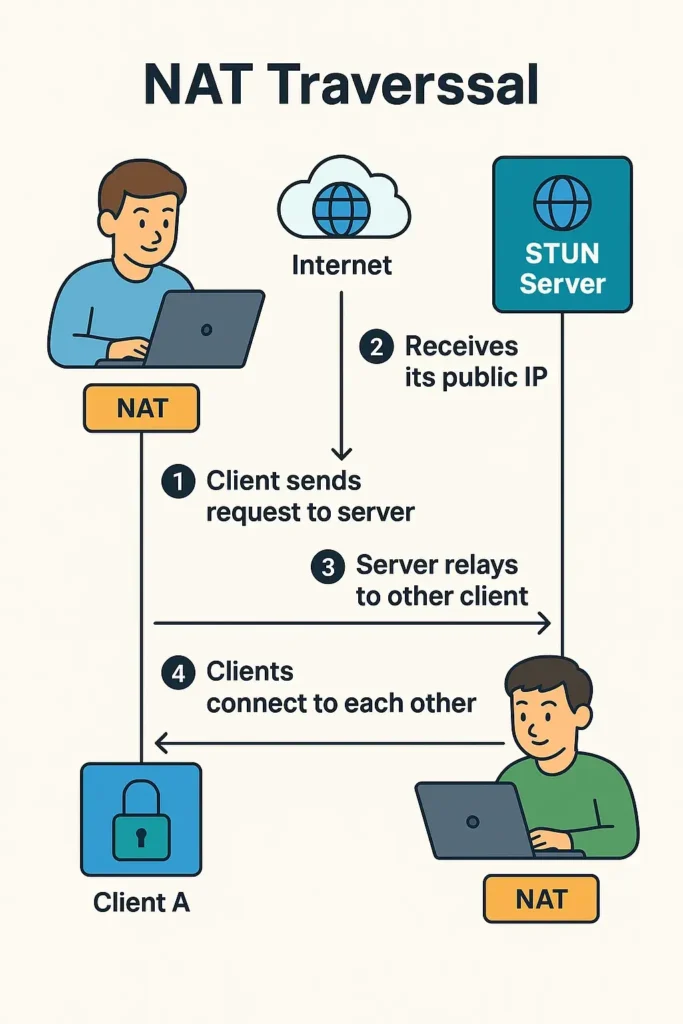
🔹 What the Diagram Shows: NAT Traversal – Step by Step
This diagram explains how two devices behind NAT routers (Client A and Client B) can communicate directly using a STUN server to “traverse” NAT.
✅ Step-by-Step Explanation:
1. Client A sends a request to the STUN server.
Client A is behind a NAT (router), so it doesn’t know its public IP address. It contacts a STUN server over the internet to ask:
“What is my public IP and port?”
2. STUN server replies with the public IP.
The server answers:
“You’re visible from the internet as IP:Port (e.g., 203.0.113.5:45678).”
3. The STUN server relays this info to Client B.
Client A and Client B both contact the same STUN server, and it shares each client’s public address with the other one.
This is key to NAT Traversal: the clients now “know how to find each other.”
4. Clients connect directly to each other.
Now, both clients send packets to each other’s public IPs and ports. If the NAT types are compatible, the connection is established directly — peer-to-peer (P2P).
💡 Why This Is Needed:
Most home and office routers block incoming connections by default.
So, two people on Zoom, WhatsApp, or any P2P app can’t connect unless they “trick” their routers into allowing it.
NAT Traversal is the trick — and it’s used in:
- Video calls (Zoom, WebRTC)
- Online games (multiplayer)
- File sharing (BitTorrent)
- VPNs and tunneling
🌐 Key Terms:
- NAT (Network Address Translation): The router hides local devices behind one public IP.
- STUN Server: Helps a device learn its public IP and port.
- TURN Server: Used when direct connection fails — it relays traffic.
- P2P (Peer-to-Peer): A direct connection between clients.
✅ NAT Security Checklist
- Disable UPnP (commonly exploited in malware attacks — Fortinet 2024).
- Disable WAN-side management.
- Pair NAT with a firewall (NAT ≠ firewall).
- Scan your public IP for exposed ports.
- Use a VPN for secure inbound connections.
- Keep firmware updated.
🔗 Part 2 — Proxy Servers
📖 The History of Proxy
Proxies were introduced in the 1990s to reduce bandwidth by caching frequently accessed content. Very quickly, their role expanded into privacy, security, and load balancing.
Today, proxies serve both defensive (protect servers) and offensive (mask clients) purposes.
🔧 How Proxies Work
The client sends a request to the proxy → The proxy forwards the request → The destination sends a response back to the proxy → The proxy sends it to the client.
🔥 Types of Proxies
- Forward Proxy: Hides clients from the internet.
- Reverse Proxy: Protects servers from direct exposure.
- Transparent Proxy: Intercepts traffic without client configuration.
- SOCKS Proxy: Works at the transport layer (TCP/UDP).
- HTTP Proxy: Only handles HTTP/HTTPS traffic.
🚩 Proxy vs VPN
| Feature | Proxy | VPN |
|---|---|---|
| IP Masking | Destination only | ISP + Destination cannot see you |
| Encryption | ❌ No | ✅ Yes |
| Coverage | App-specific | System-wide |
| Speed | Faster | Slightly slower due to encryption |
⚠️ How Hackers Abuse Proxies
- Chain multiple proxies for anonymity.
- Use open proxies for credential stuffing.
- Exploit reverse proxy misconfigurations to bypass security controls.
🛡️ Defender Tactics
- Block unauthorized outbound proxy use (CISA Alert AA24-043A).
- Deploy reverse proxies to shield servers.
- Use Deep Packet Inspection (DPI) to detect proxy patterns.
✅ Proxy Security Checklist
- Use reputable proxy providers — avoid free proxies.
- Enforce HTTPS or SOCKS proxy usage.
- Block unauthorized proxy use inside the organization.
- Protect backend servers with reverse proxies.
🛡️ Part 3 — VPN (Virtual Private Network)
📖 The Origin of VPNs
VPNs were originally developed in the mid-1990s for corporate use. Businesses needed secure channels for remote workers over the public internet.
Microsoft’s introduction of PPTP in 1996 was one of the first commercial VPN implementations. Today, VPNs are widely used for privacy, security, and bypassing censorship.
🔧 How VPN Works
A VPN creates an encrypted tunnel between your device and a VPN server. Your ISP can only see that you’re connected to the VPN. The destination sees the VPN’s IP — not yours.
📊 VPN Protocols
| Protocol | Strengths | Weaknesses |
|---|---|---|
| OpenVPN | Secure, highly configurable | Slower |
| WireGuard | Extremely fast, efficient | Newer, less audited |
| IKEv2/IPSec | Stable, fast on mobile | Less flexible on desktop |
| L2TP/IPSec | Easy to configure | Vulnerable to brute-force |
| PPTP | Very fast | Completely insecure, obsolete |
WireGuard adoption grew by 55% from 2023 to 2024 (Cisco Report).
⚠️ Common VPN Misconceptions
- VPN ≠ total anonymity.
- VPN encrypts your traffic but the VPN provider can still see your data unless it operates a strict no-log policy.
⚔️ How Hackers Abuse VPNs
- Create fake free VPNs to harvest data.
- Chain VPN servers to hide attack origins.
- Abuse commercial VPN exit nodes for spam and brute-force.
🛡️ Defender Tactics
- Block known VPN exit node IPs when necessary.
- Use behavioral analysis and CAPTCHA to detect VPN misuse.
- Enforce the use of enterprise VPNs with logging and monitoring.
✅ VPN Security Checklist
- Use a no-log VPN.
- Prefer WireGuard or OpenVPN.
- Enable kill-switch to prevent data leaks if the VPN disconnects.
- Check for DNS, IPv6, and WebRTC leaks.
- Combine VPN with hardened browsers and privacy tools.
🏰 Part 4 — Firewall
📖 The Origin of Firewalls
Firewalls emerged in the late 1980s to fill a gap in network security. The term came from physical firewalls used in architecture to prevent fires from spreading.
- 1st generation: Packet filters (1988)
- 2nd generation: Stateful firewalls (1994)
- 3rd generation: Application-layer firewalls
- Current: Next-Gen Firewalls (NGFW) with IDS/IPS, malware detection, and DPI
🔧 How Firewalls Work
- Inspect packet headers (source IP, destination IP, protocol, port).
- Apply rule sets to allow, block, log, or inspect deeper.
- Modern firewalls include Deep Packet Inspection (DPI) to look at packet contents.
🔬 DPI Pipeline Diagram
⚠️ Common Misconfigurations
- Leaving SMB (445) and RDP (3389) exposed (CISA AA24-043A).
- Allowing unrestricted outbound traffic.
- Mistakenly believing NAT is a firewall (it isn’t).
✅ Firewall Security Checklist
- Block all inbound by default.
- Block outbound except for necessary services.
- Disable UPnP.
- Use IDS/IPS and DPI.
- Regularly audit firewall logs and rule sets.
🚀 Key Facts Recap
- NAT provides privacy, not true security (Cisco 2024).
- VPN encrypts traffic; proxies don’t (Fortinet 2024).
- Firewalls don’t block phishing emails (DBIR 2024).
- The most common VPN mistake is assuming total anonymity (Cisco 2024).
- Firewalls are bypassed by port knocking, tunneling, and packet fragmentation (CISA 2024).
📚 Full Author’s Advanced Glossary
- NAT: Like a hotel receptionist managing all mail and calls for guests. Each guest has a room number (private IP), but outsiders only know the hotel’s main phone (public IP).
- Proxy: Like hiring an assistant to visit a store for you. The store only interacts with the assistant but doesn’t know who you are.
- VPN: An armored truck driving through a private tunnel. Outsiders see the truck but have no idea what’s inside or where it’s going.
- Firewall: A bouncer at a club. Checks every person trying to enter and decides whether to let them in or not based on the guest list (rules).
- TCP: Certified mail with tracking numbers and delivery confirmation. Guaranteed delivery.
- UDP: Throwing a message in a bottle. Fast, but no guarantee it arrives.
- DPI (Deep Packet Inspection): Airport security that not only checks your passport but opens your luggage, scans your shoes, and reads every item you’re carrying.
- Reverse Proxy: A receptionist at a large company. Visitors talk to the receptionist, who forwards requests internally without revealing internal details.
- NAT Traversal: Two people shouting at each other through thick walls until someone (like a STUN/TURN server) helps relay the conversation.
- Kill Switch: A safety mechanism in VPN clients that cuts all internet traffic if the VPN disconnects, preventing data leaks.
- UPnP (Universal Plug and Play): A convenience feature that automatically opens ports on routers — often abused by malware.
🏁 Conclusion
The internet wasn’t built with security in mind — but you no longer have an excuse not to be secure. NAT, proxies, VPNs, and firewalls are your defensive perimeter.
Used correctly, they are incredibly powerful. Misconfigured, they are worthless. Hackers already know how to exploit weaknesses in these systems. Your job is to be smarter.
Master them. Harden them. Stay safe