⚡ Beneath the Screen: The Secret Life of Data
You open your laptop. A browser launches. You type google.com and press Enter.
In less than a second, your screen fills with color, content, answers. It feels instant. Effortless. Like magic.
But under the hood, a complex ballet unfolds — one involving invisible addresses, binary packets, handshake protocols, and routers spanning continents. Every website you visit, every video you stream, every message you send is a result of thousands of micro-decisions made by machines, governed by strict rules that never sleep.
The internet isn’t just a cloud. It’s math. Electricity. Cables on the ocean floor.
And understanding how it works isn’t just for engineers — it’s for anyone who wants to take control of their digital world.
This guide is your decoder ring: IPs, DNS, TCP/IP, routing, packets, and protocols — explained in real terms, with real-world threats and modern relevance. Written by cybersecurity analysts, simplified for smart humans.
Let’s unpack the most important invention since electricity.
⚠️ Disclaimer
This article is written for educational and ethical purposes only. Its goal is to help readers understand how networks and internet protocols function in order to improve digital literacy, cybersecurity awareness, and safe usage of online systems.
It does not promote or support any malicious activity, unauthorized access, or misuse of networking knowledge. Always act in accordance with your local laws and best practices in cybersecurity.
👤 What Is a Computer Network?
A network is a group of devices (computers, phones, servers, routers) that communicate to share data.
- Your home Wi-Fi is a local network.
- The internet is a network of networks.
🚀 IP Address — The Digital Identity
🔎 What Is an IP Address?
An Internet Protocol (IP) address is like a street address for your device online. It identifies where your device is and where to send or receive data.
📁 IPv4 vs IPv6
- IPv4 (Internet Protocol version 4) — A 32-bit address written in dotted decimal format (e.g.,
192.168.1.1). Provides ~4.3 billion addresses. Running out fast. - IPv6 (Internet Protocol version 6) — A 128-bit address written in hexadecimal (e.g.,
2001:0db8:85a3:0000:0000:8a2e:0370:7334). Provides 340 undecillion addresses (3.4 x 10^38) — solves the shortage.
IPv6 improvements:
- Built-in security features.
- Simplifies routing.
- No need for NAT.
🔢 Public vs Private IP
- Public IP: Visible to the internet. Assigned by your ISP (Internet Service Provider).
- Private IP: Used inside your home or office network (ranges like
192.168.x.x,10.x.x.x).
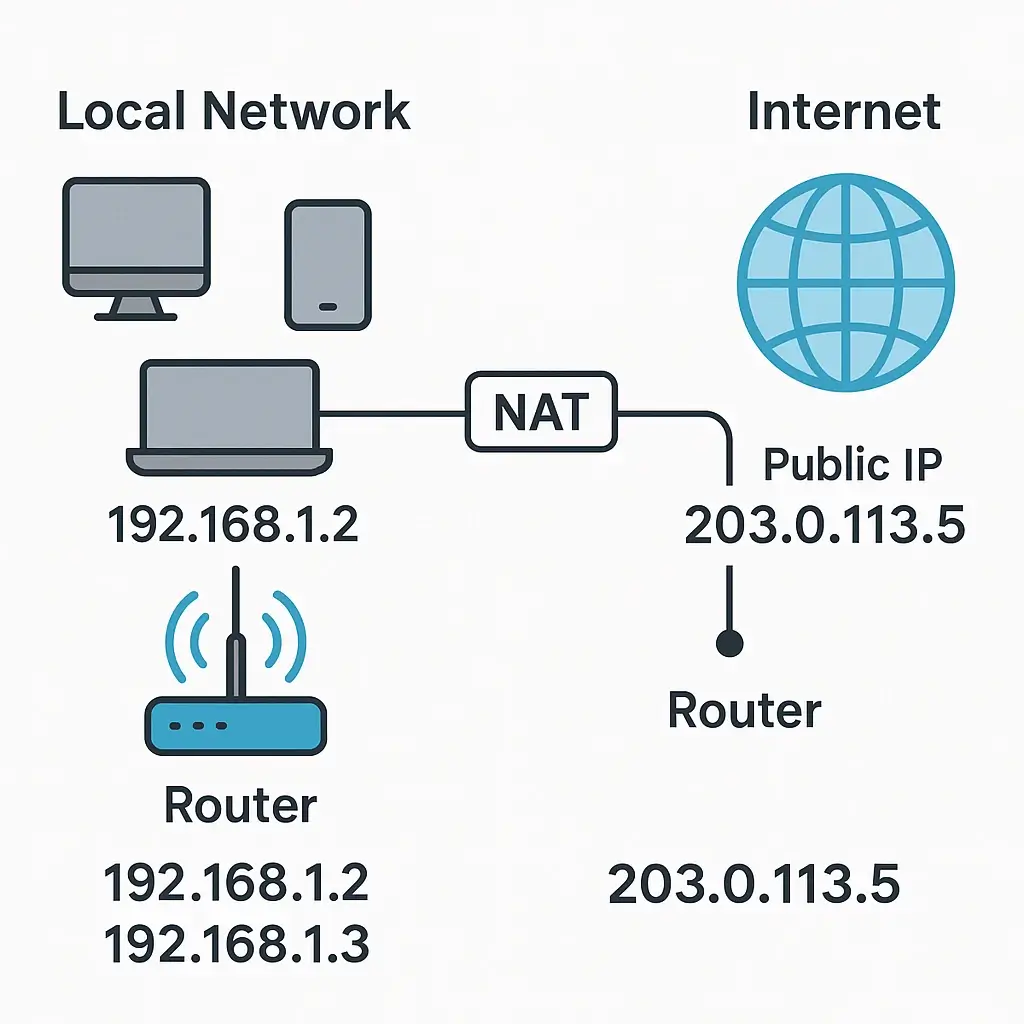
📁 NAT (Network Address Translation) — The Internet’s Workaround
🏛️ Why NAT Exists
IPv4 doesn’t have enough addresses. NAT allows multiple devices on a private network to share one public IP.
🔎 How NAT Works
- Router replaces private IP with public IP for outbound traffic.
- Keeps a translation table to send return traffic to the correct device.
📊 Types of NAT
- Static NAT: One private IP maps to one public IP.
- Dynamic NAT: Assigns available public IPs dynamically.
- PAT (Port Address Translation): Most common. Multiple private IPs share one public IP but use different ports.
🚩 Issues with NAT
- Breaks peer-to-peer connections.
- Causes problems for VPNs and VoIP.
- IPv6 removes the need for NAT entirely.
📚 DNS — The Internet’s Phonebook
🔎 What Is DNS?
The Domain Name System (DNS) translates human-readable domains (e.g., google.com) into IP addresses computers understand.
🌐 How DNS Works
- You type
google.com. - Your device asks a DNS Resolver.
- Resolver checks cache. If not found:
- Queries Root DNS Server.
- Root server points to TLD (Top-Level Domain) server (e.g.,
.com). - TLD points to Authoritative DNS for Google.
- Resolver gets the IP and returns it to your browser.
- Cached for next time.
🚩 DNS Vulnerabilities
- DNS Spoofing/Cache Poisoning: Fake DNS responses redirect you to malicious sites.
- DNS Hijacking: Attackers reroute DNS queries via malware or compromised routers.
- DNS Amplification (DDoS): Exploits DNS to flood targets with traffic.
- Man-in-the-Middle (MITM) DNS: Attackers intercept DNS queries on insecure networks.
🔒 DNS Protections
- DNSSEC (Domain Name System Security Extensions): Authenticates DNS data.
- DNS-over-HTTPS (DoH) and DNS-over-TLS (DoT): Encrypt DNS traffic.
- Use trusted resolvers like Cloudflare (
1.1.1.1) or Google (8.8.8.8).
🚁 TCP/IP Stack — How Data Travels
📆 TCP vs UDP
- TCP (Transmission Control Protocol):
- Reliable, ordered, error-checked.
- Establishes connection with a 3-way handshake: SYN → SYN-ACK → ACK.
- Used for websites, email, file transfers.
- UDP (User Datagram Protocol):
- Faster but no guarantee of delivery or order.
- Used for gaming, video calls, streaming.
🌟 TCP Flags
- SYN: Initiate connection.
- ACK: Acknowledge.
- FIN: Finish connection.
- RST: Reset.
- PSH: Push data immediately.
- URG: Urgent data.

🔁 ASCII-схема: TCP 3-Way Handshake
Client Server
| SYN (request) |
| ────────────────────────────> |
| |
| SYN-ACK (accept) |
| <──────────────────────────── |
| |
| ACK (confirm) |
| ────────────────────────────> |
| |
| ✅ Connection Established |
📘 This is how reliable communication begins between two devices — the foundation of HTTP, email, and most secure transactions.
🌐 Routing — How Packets Find Their Way
🔍 What Is Routing?
Routing is how data packets move from one network to another.
🚌 How Routing Works
- Routers check destination IP.
- Forward packets based on routing tables.
📣 Routing Protocols
- OSPF (Open Shortest Path First): Internal networks.
- BGP (Border Gateway Protocol): Internet-wide routing between ISPs.
🚩 Routing Issues
- BGP hijacks cause major internet outages.
- Misconfigurations can reroute global traffic (Facebook outage 2021).
📦 Data Packets — The Units of Internet
📆 What Is a Packet?
A packet is a small piece of data sent over a network.
- Header: Source/Destination IP, Port.
- Payload: The actual data (website, email, file).
- Trailer: Error-check info.
📚 Packet Terms
- Frame: Physical/Data Link layer.
- Segment: TCP layer.
- Datagram: UDP packet.
🌎 Example: Visiting google.com
- DNS resolves
google.comto an IP. - TCP handshake starts (SYN, SYN-ACK, ACK).
- HTTP(S) request sent: “GET /index.html”.
- Data split into packets.
- Packets routed via ISPs and internet backbone.
- Google replies → Packets take fastest route back.
- Browser assembles packets into a webpage.
🚩 Security Risks Recap
- DNS Spoofing, Hijacking, MITM.
- Packet Sniffing (especially on public Wi-Fi).
- ARP Spoofing (redirect local traffic).
- BGP Hijacking (global misroutes).
🔒 Mitigation:
- VPN, HTTPS, Secure DNS, strong router security.
🧬 OSI Model Explained: The Blueprint of Networking
Before the web became wireless and invisible, engineers needed a blueprint — a way to describe how data moves from one device to another. That blueprint is the OSI Model — a seven-layer framework that breaks networking into understandable parts.
It’s not how the internet literally works — but it’s how we understand it when something breaks.
📐 The 7 Layers of the OSI Model
| Layer | Name | Function | Examples |
|---|---|---|---|
| 7 | Application | User-facing interface for network services | HTTP, FTP, SMTP, DNS |
| 6 | Presentation | Data formatting, encryption, compression | SSL/TLS, JPEG, ASCII |
| 5 | Session | Opens, manages, closes connections (sessions) | APIs, NetBIOS, RPC |
| 4 | Transport | Reliable data delivery with error handling | TCP, UDP |
| 3 | Network | Logical addressing and path selection | IP, ICMP, BGP, OSPF |
| 2 | Data Link | Frame delivery between devices on same network | Ethernet, MAC addresses, ARP |
| 1 | Physical | Physical transmission (electrical, optical, etc.) | Cables, Wi-Fi, fiber, radio |
🛠 Why It Still Matters
- Troubleshooting: Is the problem physical (Layer 1), network-related (Layer 3), or an app misconfig (Layer 7)?
- Security: Firewalls filter at Layer 4; SSL operates at Layer 6.
- Diagnostics: Packet analyzers (like Wireshark) show which layer is misbehaving.
🔄 OSI vs TCP/IP
Modern internet protocols (like TCP/IP) combine these layers, but OSI gives us a clear mental map.
🧠 Tip: Think of the OSI model like postal mail:
- Layer 7: You write a letter.
- Layer 4: It’s broken into envelopes.
- Layer 3: The envelopes are addressed.
- Layer 1: They’re physically delivered.
📊 OSI vs TCP/IP Model — Simplified Mapping
| OSI Layer | TCP/IP Layer | Example Protocols |
|---|---|---|
| Application | Application | HTTP, HTTPS, DNS, FTP |
| Presentation | — | SSL/TLS (Encryption) |
| Session | — | RPC, APIs, NetBIOS |
| Transport | Transport | TCP, UDP |
| Network | Internet | IP, ICMP, ARP |
| Data Link | Link | Ethernet, PPP |
| Physical | Physical | Cables, Wi-Fi, Fiber |
🧠 Note: The TCP/IP model is more practical and less granular. OSI is a conceptual framework, often used in education and diagnostics.
🌟 Final Thoughts
The internet isn’t magic — it’s packets, protocols, and pathways. Understanding how it works is the first step to mastering cybersecurity.