🧠 What Is Encryption and Why It Matters
Imagine sending a letter through the mail. Anyone handling it along the way could read its contents unless you place it inside a sealed envelope. Encryption is the digital version of that envelope — but far stronger.
At its core, encryption is the process of converting readable data (plaintext) into an unreadable format (ciphertext) using mathematical algorithms. Only someone with the correct key can decrypt the message and read the contents.
⚠️ Disclaimer
This article is written for educational and ethical purposes only. Its goal is to help readers understand how encryption works to improve privacy, protect data, and enhance cybersecurity awareness. The information provided is not intended for illegal use.
🔥 Why Encryption Exists:
- 🛡️ Protects sensitive information from hackers, governments, ISPs, and cybercriminals.
- 🔒 Ensures confidentiality for personal messages, bank transactions, and business communications.
- ✔️ Forms the backbone of internet security — including websites, emails, messaging apps, and cloud storage.
Without encryption, the internet would be a dangerous place where passwords, credit cards, and private conversations could be stolen by anyone.
📜 A Brief History of Encryption
Encryption isn’t new. Humans have been using codes and ciphers for thousands of years:
- The Caesar Cipher was used by Julius Caesar to encode military messages.
- During World War II, the Enigma machine helped the Germans encrypt their communications — famously cracked by Alan Turing’s team, changing the course of the war.
Modern encryption, however, is based on complex mathematics rather than simple substitution or mechanical devices. The introduction of computers in the 20th century made encryption far more sophisticated — and necessary.
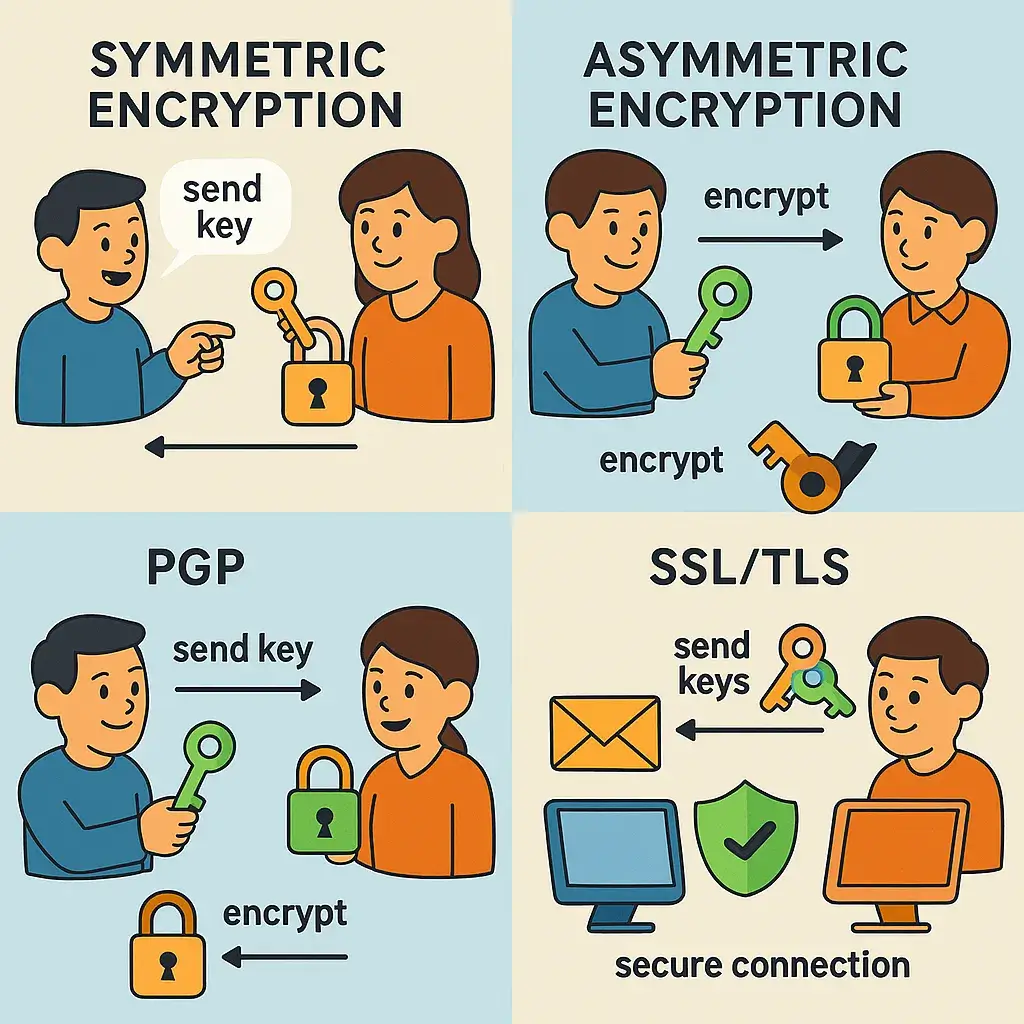
🔑 Two Main Types of Encryption: Symmetric and Asymmetric
🔐 1. Symmetric Encryption — One Key to Rule Them All
🔸 How It Works:
Symmetric encryption uses a single key to both encrypt and decrypt data. The sender and receiver must both have the same key — and keep it secret.
| Sender | ➡️ | Encrypted Data | ➡️ | Receiver |
|---|---|---|---|---|
Encrypts with Key X | Decrypts with Key X |
🔸 Advantages:
- ✅ Fast and efficient — great for encrypting large amounts of data.
- ✅ Uses less computational power than asymmetric encryption.
🔸 Disadvantages:
- ⚠️ Key distribution problem — if someone intercepts the key, the encryption is broken.
- Not scalable for large networks where many users need secure communication.
🔸 Examples of Symmetric Encryption Algorithms:
- AES (Advanced Encryption Standard) — The current industry standard (used in everything from Wi-Fi to government security).
- DES (Data Encryption Standard) — Now obsolete, replaced by AES.
- Blowfish, Twofish, ChaCha20 — Other examples.
🔑 2. Asymmetric Encryption — The Magic of Public and Private Keys
🔸 How It Works:
Asymmetric encryption uses two different keys:
- A public key (shared with everyone).
- A private key (kept secret).
| Sender | ➡️ | Encrypted Data | ➡️ | Receiver |
|---|---|---|---|---|
Encrypts with Public Key A | Decrypts with Private Key A |
- Anyone can encrypt data using the recipient’s public key, but only the recipient can decrypt it using their private key.
🔸 Advantages:
- ✅ Solves the key distribution problem.
- ✅ Provides authentication — confirms the identity of the sender.
🔸 Disadvantages:
- ⚠️ Slower than symmetric encryption.
- ⚠️ Requires more processing power — not ideal for encrypting large amounts of data directly.
🔸 Examples of Asymmetric Algorithms:
- RSA (Rivest–Shamir–Adleman) — Most common.
- ECC (Elliptic Curve Cryptography) — Faster and more secure with smaller keys.
- Diffie-Hellman — Used for key exchange.
📬 What Is PGP (Pretty Good Privacy)?
🔁 ASCII Diagram — PGP Encryption Flow
mathematica[Plaintext Message]
|
[Encrypt with Symmetric Key]
|
[Encrypted Message]
|
[Encrypt Symmetric Key with Recipient's Public Key]
|
+---------------------------+
| Encrypted Message Packet |
| + Encrypted Symmetric Key|
+---------------------------+
↓
[Send to Recipient]
↓
[Decrypt Symmetric Key with Private Key]
↓
[Decrypt Message with Symmetric Key]
↓
[Plaintext Restored]
🔸 Overview:
PGP is an encryption system used primarily for securing email communication. It combines the strengths of both symmetric and asymmetric encryption.
🔸 How It Works:
- The message itself is encrypted with a symmetric key (fast).
- This symmetric key is then encrypted using the recipient’s public key (secure distribution).
- The recipient uses their private key to decrypt the symmetric key and then decrypts the message.
🔸 Features:
- ✉️ Email encryption.
- 🔏 Digital signatures for authenticity.
- 🔐 Secure file encryption.
🔸 Is PGP Still Relevant?
Yes. PGP and its open-source alternative GPG (GNU Privacy Guard) are widely used for secure communications among journalists, activists, businesses, and cybersecurity professionals.
🌐 What Is SSL/TLS? — Encryption for the Internet
🔸 Definition:
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are encryption protocols that secure connections over the internet — like when you visit a website starting with https://.
КопироватьРедактировать
🔸 How It Works:
- When you visit a website, your browser and the web server perform an SSL/TLS handshake, which involves:
- Exchanging public keys.
- Verifying digital certificates.
- Creating a shared session key (symmetric encryption for the session).
🔐 ASCII Diagram — TLS Handshake (Simplified)
Client Server
| |
| ---- Client Hello -----------> |
| |
| <--- Server Hello, Cert ------ |
| |
| ---- Key Exchange / Pre-Master |
| |
| <--- Finished (Encrypted) ---- |
| ---- Finished (Encrypted) ---> |
| |
[Secure Encrypted Communication Established]
🔸 SSL/TLS Uses:
- 🛒 Secure online shopping and banking.
- 📧 Protecting logins and personal information.
- 🔐 Securing VPN connections, VoIP, and APIs.
🔸 Is SSL Still Used?
No. SSL is obsolete. (TLS superseded SSL, but many still say “SSL” colloquially. )Modern websites use TLS 1.2 or TLS 1.3, which are faster and more secure. However, the term “SSL” is still commonly used colloquially.
📊 Comparison Table — Encryption Models
| Feature | Symmetric Encryption | Asymmetric Encryption | PGP (Hybrid) | SSL/TLS (Hybrid) |
|---|---|---|---|---|
| Key Type | One shared key | Public + private keys | Both (Sym + Asym) | Both (Sym + Asym) |
| Speed | ✅ Very fast | 🐢 Slower | ⚡ Balanced | ⚡ Fast after handshake |
| Security | 🔓 Vulnerable if key leaked | 🔐 Strong | 🔐 Strong | 🔐 Strong |
| Use Case | File encryption, Wi-Fi | Email, authentication | Secure email, file sharing | Web, APIs, HTTPS |
| Key Distribution | ❌ Difficult (must be secret) | ✅ Easy (public key sharing) | ✅ Easier with public keys | ✅ Handshake + certificate |
| Real-World Example | AES in 7-Zip | RSA in SSH | GPG, ProtonMail | TLS in HTTPS websites |
📦 Real-World Use Cases of Encryption
| Platform | Encryption Type | Description |
|---|---|---|
| End-to-end (E2EE) via Signal Protocol | Uses asymmetric encryption to exchange session keys, then symmetric (AES) for message exchange. | |
| ProtonMail | PGP-based Email | Encrypts and signs emails using open PGP standard. |
| HTTPS Everywhere | SSL/TLS Hybrid | Ensures all connections are over HTTPS (TLS 1.2+). |
| Disk Encryption (BitLocker, VeraCrypt) | Symmetric (AES) | Encrypts local data with strong symmetric ciphers. |
| VPN Services | TLS + AES | Encrypts internet traffic between client and VPN server. |
| SSH (Secure Shell) | Asymmetric + Symmetric | Authenticates with keys, then establishes a secure symmetric session. |
⚠️ Examples of Misconfigurations and Vulnerabilities
| Mistake | Risk / Attack Type | Example |
|---|---|---|
| Using SSL instead of TLS | 🧨 Outdated protocol with known exploits | SSLv3 vulnerable to POODLE |
| Weak cipher suites allowed | 🔓 Can be forced to downgrade (cipher suite downgrade) | TLS with RC4 enabled |
| Self-signed certificate (untrusted CA) | ❌ Can be spoofed or intercepted | MitM with rogue certificate |
| No certificate pinning | 👀 Susceptible to CA compromise | Fake cert from malicious CA |
| Not verifying cert expiration | ⏳ Outdated certs can be accepted | No revocation checking = spoofing |
| Sending data over HTTP | 📡 Credentials or data can be intercepted | Login page over plain HTTP |
✅ Checklist for Encryption Best Practices
- 🔒 Always use HTTPS websites (SSL/TLS).
- 🔐 Encrypt sensitive files with tools like VeraCrypt or 7-Zip (AES).
- 📬 Use PGP for truly private email — don’t rely on just password-protected accounts.
- 🔑 Use strong, modern encryption algorithms (AES-256, RSA-2048+, ECC).
- 🛑 Never use outdated protocols like SSL, DES, or MD5.
- 📜 Verify the authenticity of public keys before using them.
📚 Author’s Glossary
- Encryption: The process of converting readable data (plaintext) into unreadable data (ciphertext).
- Plaintext: Data in its readable form.
- Ciphertext: Data that has been encrypted.
- Symmetric Encryption: Encryption where the same key is used for both encryption and decryption.
- Asymmetric Encryption: Encryption that uses a public key for encryption and a private key for decryption.
- PGP (Pretty Good Privacy): A hybrid encryption method combining symmetric and asymmetric encryption for email and file protection.
- SSL/TLS: Protocols that encrypt data between browsers and servers for secure internet communication.
- Key: A string of data used by encryption algorithms to lock (encrypt) or unlock (decrypt) information.
- Handshake: The process where two parties establish encryption keys for secure communication.
- Certificate: A digital document verifying the ownership of a public key, issued by a Certificate Authority (CA).
🏁 Conclusion
Encryption is the foundation of modern cybersecurity. Whether it’s protecting your emails with PGP, securing your internet traffic with TLS, or locking sensitive files with AES, encryption ensures privacy and safety in a connected world.
Understand it. Use it. Stay secure.