Last Updated: July 2025
⚠️ Disclaimer
This article is written for educational and ethical purposes only. Its goal is to help readers understand cloud security risks and learn best practices to prevent data breaches and unauthorized access.
🔍 Introduction
The shift to cloud computing has transformed how individuals and businesses store, access, and manage data. While the benefits are enormous—scalability, availability, and cost-efficiency—cloud environments also introduce unique security risks. From misconfigurations to insider threats, the vulnerabilities are often overlooked or misunderstood. This guide dives deep into real-world threats and gives actionable strategies to protect your assets in the cloud.
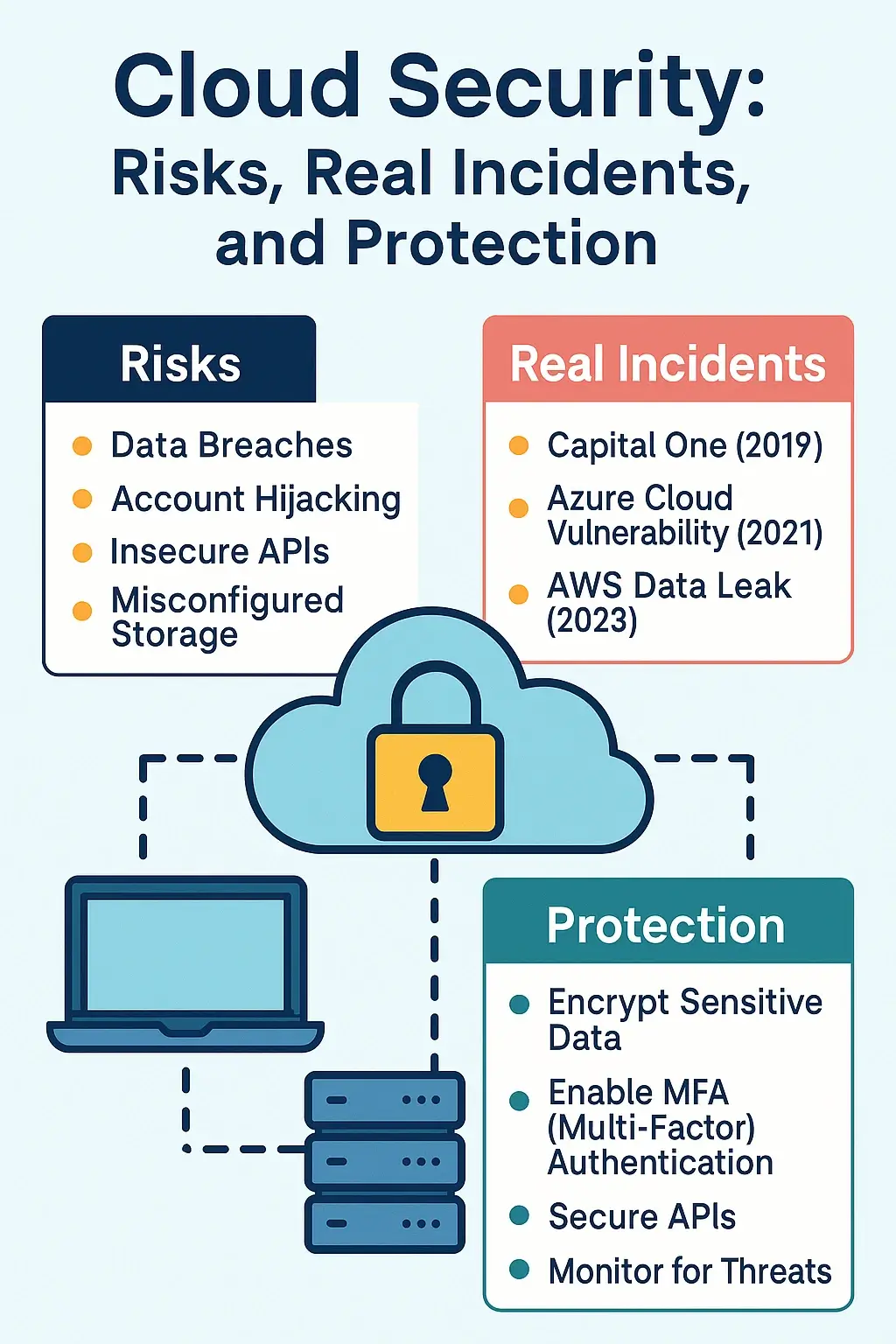
🧨 Real Risks in the Cloud
1. 🔓 Misconfigured Cloud Storage
Cloud storage buckets (e.g., Amazon S3, Google Cloud Storage) are often left publicly accessible by mistake. This has led to numerous breaches.
Example: In 2017, Accenture, a Fortune Global 500 company, exposed highly sensitive data in four open AWS S3 buckets. The leak included API data, certificates, and authentication credentials.
Mitigation:
- Enable encryption by default.
- Set strict access permissions.
- Use cloud provider’s configuration audit tools (e.g., AWS Config, Azure Policy).
2. 👤 Insider Threats
Not all attacks come from the outside. In 2019, Capital One—a major U.S. bank—experienced a massive breach caused by a former AWS engineer, Paige A. Thompson.
She exploited a Web Application Firewall (WAF) misconfiguration and gained access to Amazon S3 buckets, leaking over 100 million records.
Mitigation:
- Immediately revoke employee credentials upon termination.
- Implement least privilege access.
- Use behavioral analytics to monitor insider activity.
- Enable real-time alerts for unusual cloud behavior.
3. 🦠 Insecure APIs
APIs are essential in cloud environments but often lack proper authentication or rate-limiting, leaving systems open to exploitation.
Example: In 2018, a T-Mobile API flaw exposed personal data (including IMSI numbers) of around 2 million customers due to improper authentication.
Mitigation:
- Use OAuth 2.0 and implement rate limiting.
- Regularly audit API endpoints.
- Implement API gateways with built-in security policies.
4. 🧫 Malware in the Cloud
Cloud-hosted apps can be infected with malicious scripts that spread to end users. Attackers often upload infected files or execute code inside virtual machines.
Mitigation:
- Enable file scanning tools (e.g., Amazon GuardDuty).
- Regularly patch cloud workloads and VMs.
- Use cloud-native firewalls and WAFs.
5. 🪤 Shadow IT
Employees sometimes deploy their own cloud services without IT approval, creating major security blind spots. This practice is especially common in remote and hybrid work environments.
Mitigation:
- Educate employees about cloud security risks.
- Use CASBs (Cloud Access Security Brokers) to detect third-party app usage.
- Enforce centralized authentication systems.
🔐 Layer Explanation:
+-----------------------------+
| Cloud Dashboard |
| (e.g., AWS Console) |
+-----------------------------+
|
▼
+-----------------------------+
| Identity & Access Mgmt |
| (IAM, MFA, RBAC) |
+-----------------------------+
|
▼
+-----------------------------+
| Virtual Private Cloud |
| (Subnets, ACLs) |
+-----------------------------+
| |
+------+-----+ +------+-----+
| Public | | Private |
| Subnet | | Subnet |
+-------------+ +-------------+
| |
+----------+ +-------------+
| Firewall | | App Servers |
| (WAF) | | DB Instances|
+----------+ +-------------+
|
+------------+
| S3 Bucket | ← (Private, Encrypted)
+------------+
Cloud Dashboard: Management interface (e.g., AWS/Azure/GCP console).
IAM (Identity & Access Management): Defines who has access to what. Use MFA and least privilege principles.
VPC (Virtual Private Cloud): Network-level isolation to separate resources securely.
Public Subnet: Hosts internet-facing resources (e.g., load balancers), protected by WAF.
Private Subnet: Hosts sensitive services like databases and internal apps.
Firewall / WAF: Filters and blocks malicious HTTP/S traffic.
S3 Bucket: Must be explicitly made private and encrypted (at rest and in transit).
✅ Essential Checklist for Cloud Security
| Task | Description |
|---|---|
| 🔐 Use Multi-Factor Authentication | Protect logins with additional security layers. |
| 🧱 Enable Firewalls and VPCs | Isolate workloads and control inbound/outbound traffic. |
| 📦 Encrypt Data at Rest and In Transit | Use AES-256 and TLS for comprehensive encryption. |
| 📊 Monitor Logs in Real Time | Use tools like CloudTrail (AWS) or Azure Monitor. |
| ⚠️ Auto-Alert Misconfigurations | Enable cloud-native alerting systems for exposure events. |
🔐 Advanced Protection Techniques
🧩 Secure Configuration
- Use Infrastructure-as-Code (IaC) tools like Terraform and CloudFormation.
- Integrate cloud security scanners like Prowler, ScoutSuite, or CloudMapper.
- Apply automated security baselines using CIS Benchmarks.
🧠 Threat Modeling
- Simulate real-world attack scenarios.
- Conduct red team assessments.
- Identify privilege escalation paths and lateral movement potential.
📥 Backup & Recovery
- Automate backup schedules.
- Use object versioning in storage buckets.
- Test restore procedures regularly to ensure reliability.
📤 Identity and Access Management (IAM)
- Follow the Principle of Least Privilege (PoLP).
- Rotate access keys and tokens.
- Use role-based access control (RBAC) and temporary credentials.
📚 Sources
- Capital One Breach (The Verge, July 2019)
- Accenture S3 Exposure (UpGuard, 2017)
- T-Mobile API Vulnerability (TechCrunch, 2018)
- OWASP Cloud Top 10
- NIST Cloud Computing Guidelines
❓ FAQ: Cloud Security Fundamentals
What is Shadow IT and why is it dangerous?
Shadow IT refers to unapproved cloud apps or services used by employees. It’s dangerous because IT teams can’t monitor or secure what they don’t know exists.
Why is IAM so important in the cloud?
Improper identity and access controls are a leading cause of cloud breaches. IAM ensures only authorized users can access specific resources.
Can public buckets be made private after data is exposed?
Yes, but the damage may already be done. Proactive prevention is critical.
What’s the difference between VPC and firewall?
A VPC isolates your cloud network. Firewalls control traffic in/out of subnets and instances inside that VPC.
How often should cloud configs be audited?
At least monthly. Ideally, automated scanners should run continuously.
🧠 Glossary
| Term | Explanation |
| S3 Bucket | Cloud storage container used in AWS for storing files and data. |
| IAM | Identity and Access Management — controls who can access what in the cloud. |
| WAF | Web Application Firewall — filters incoming traffic to protect apps. |
| CASB | Cloud Access Security Broker — tool that monitors and enforces security policies across cloud services. |
| OAuth 2.0 | Authorization framework allowing apps to access data without sharing passwords. |
| Multi-Tenant | A single cloud instance shared by multiple users or organizations. |
| Shadow IT | Unapproved tech used by employees that escapes IT oversight. |