🎯 Learn How Hackers Trick People — and How to Outsmart Them
💥 Introduction: The Bait Has Evolved — But You’re Still the Target
It doesn’t start with a breach. It starts with a message.
A simple email, a friendly voice on the phone, a text that seems urgent but familiar. You hesitate — just for a second — and that’s all it takes. In 2025, cyberattacks don’t break down firewalls. They walk through the front door you forgot to lock. And more often than not, that door is you.
Phishing has become the lingua franca of digital deception. But its modern variants — vishing (voice phishing) and smishing (SMS phishing) — are more than just annoying scams. They’re precision-engineered psychological traps. Blending social engineering with real-time data leaks, today’s attacks are personalized, automated, and terrifyingly effective.
And unlike spam from a decade ago, these aren’t riddled with typos or sent from sketchy addresses. They mimic your boss’s tone, spoof your bank’s number, and sometimes even use your own voice — deepfaked.
This guide will take you beyond definitions. We’ll dissect real-world examples, expose the mechanics behind each attack, and show you exactly how to recognize — and resist — the modern face of digital manipulation.
Because in the phishing wars, the first casualty is trust.
⚠️ Disclaimer
This article is written for educational and ethical purposes only. Its purpose is to help readers recognize and protect themselves against phishing, vishing, and smishing attacks
🚩 What Is Phishing?
Phishing is a cyberattack where criminals pretend to be someone you trust. They try to trick you into revealing sensitive information, such as passwords, credit card numbers, or login credentials.
Typically, phishing happens via email. However, attackers also use websites, social media, or even apps to deliver their traps.
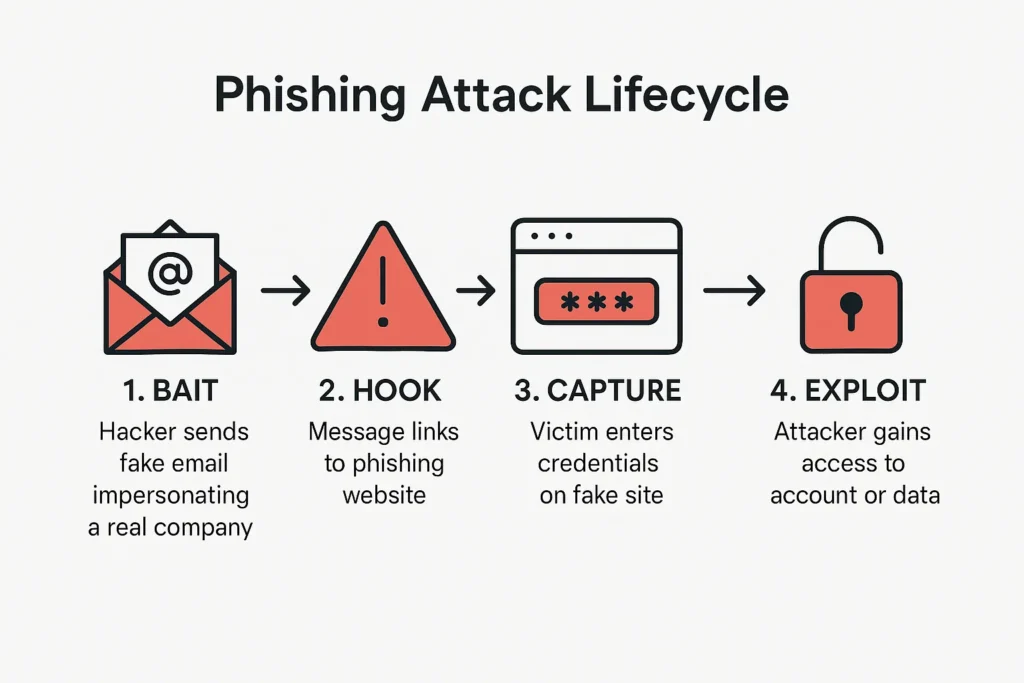
🏴☠️ How Does Phishing Work?
Let’s break it down step by step:
- Step 1: You receive an email that looks like it comes from a legitimate company — for instance, Amazon, PayPal, or your bank.
- Step 2: The message creates a sense of urgency. It tells you to verify your account, reset your password, or confirm a payment.
- Step 3: A fake link directs you to a cloned website designed to steal your login credentials.
- Step 4: Once you enter your information, hackers instantly capture it and access your account.
🕰️ Timeline of Major Phishing Incidents in Cybersecurity History
| 📅 Year | 🎯 Incident | 🔍 What Happened |
|---|---|---|
| 1996 | First Recorded Phishing Attack (AOL) | Hackers impersonated AOL staff to steal user passwords via fake login prompts — the birth of phishing. |
| 2003 | Term “Phishing” Coined | The word “phishing” enters the cybersecurity lexicon, combining “fishing” with “phreaking.” |
| 2005 | PayPal & eBay Phishing Surge | Large-scale phishing campaigns mimicked PayPal/eBay login pages, marking the rise of mass credential harvesting. |
| 2011 | RSA Breach via Phishing | A malicious Excel file exploited a Flash vulnerability in an employee email, compromising RSA’s SecurID system. |
| 2013 | Target Breach (40M Cards) | Attackers gained access via a phishing email sent to a third-party HVAC vendor. Result: 40 million cards exposed. |
| 2014 | Sony Pictures Hack | Spear phishing gave North Korean attackers internal access, resulting in leaked emails and unreleased films. |
| 2016 | DNC Hack (US Elections) | Russian state-sponsored actors used phishing to steal credentials of top Democratic Party officials. |
| 2017 | Google Docs Worm | A worm disguised as a Google Docs invite spread rapidly, granting access to Gmail accounts. Over 1 million affected. |
| 2020 | COVID-19 Phishing Spike | Global crisis used as bait: fake WHO emails, relief fund scams, vaccine registration phishing boomed. |
| 2021 | Colonial Pipeline Attack | Though the breach began with credential theft, phishing emails were used to gain deeper access. Led to fuel shortages. |
| 2023 | Twilio & Cloudflare SMS Phishing | Sophisticated smishing campaign used fake login portals; Twilio confirmed employee compromise. |
| 2024 | Deepfake Vishing Attacks | Executives tricked by AI-generated voices impersonating their CEO; funds transferred in multiple high-profile cases. |
| 2025 | QR Code Phishing (“Quishing”) Boom | Phishing evolves: malicious QR codes in emails and public posters lead users to spoofed logins. Still rising. |
🔥 Real-World Example — Email Phishing
Subject: Your PayPal Account Is Limited — Immediate Action Required!
“Dear user,
We noticed unusual activity on your PayPal account. Please verify your identity immediately, or your account will be suspended.
Click here to resolve the issue → [fake-paypal.com/login]”
At first glance, the email seems legitimate. The link opens a webpage that looks identical to PayPal’s login page. Unsuspecting victims enter their credentials, and attackers quickly hijack their accounts.
🚨 How to Spot Email Phishing
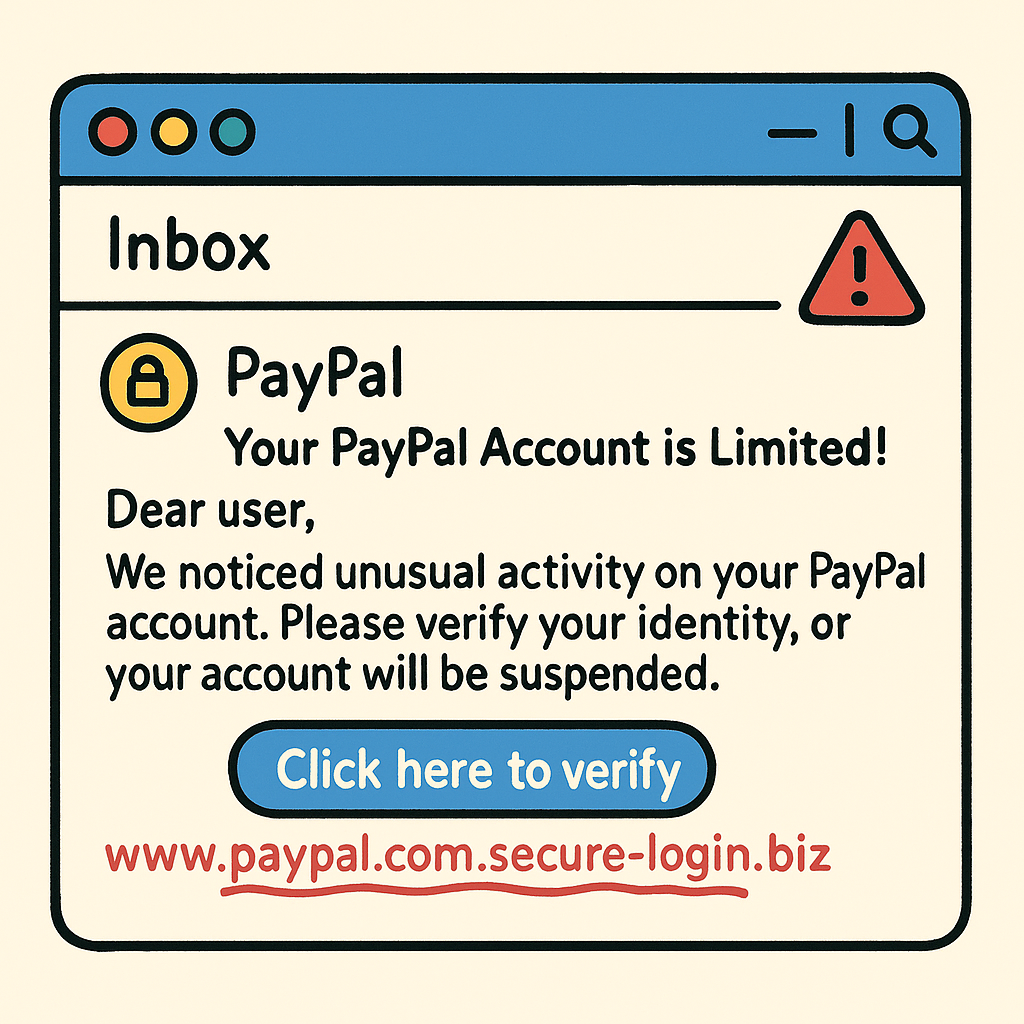
Look for these warning signs:
- 🟥 Urgency: Phrases like “Immediate action required” or “Account suspended” pressure you to act without thinking.
- 🟥 Generic greetings: “Dear user” instead of your actual name is a huge red flag.
- 🟥 Suspicious links: Hover over the link — does the URL match the official website? Often, it doesn’t.
- 🟥 Grammar mistakes: Poor spelling or strange phrasing signals a scam.
- 🟥 Weird sender address: Check for slight variations like security@paypa1,com (using a “1” instead of “l”).
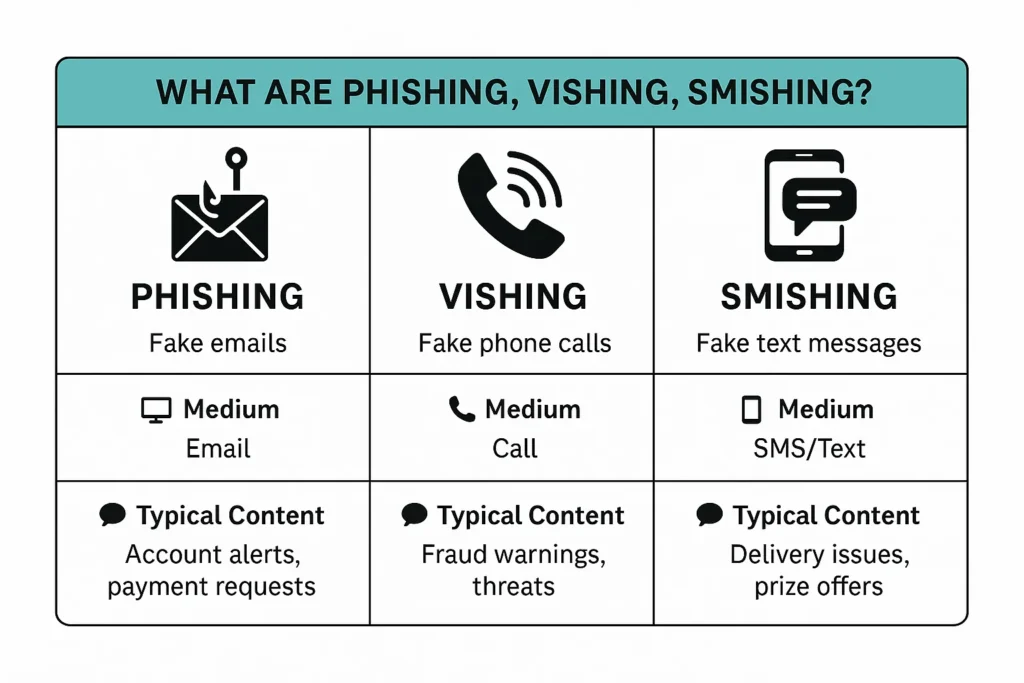
📲 What Is Smishing?
Smishing stands for SMS phishing. Attackers send fake text messages that aim to steal your personal information, just like email phishing does.
What’s more, smishing often feels more convincing because people tend to trust text messages more than emails.
🔥 Real Example — Smishing
Message:
“Your FedEx delivery is on hold. Confirm your address here:
[fedex-delivery-check.com]”
When victims click the link, they land on a fake webpage. It asks for personal information like your name, address, and sometimes payment details. Worse yet, some links directly install malware onto the phone.
🚨 How to Recognize Smishing
Pay attention to these clues:
- 🟧 Texts from unknown numbers demanding urgent action
- 🟧 Links that don’t match the real company’s domain
- 🟧 Messages offering unrealistic prizes — “You’ve won an iPhone!”
- 🟧 Obvious grammar mistakes or broken English
📞 What Is Vishing?
Vishing stands for voice phishing. Cybercriminals call you while pretending to be someone from your bank, a government agency, tech support, or even your company’s IT department.
The goal remains the same: trick you into revealing sensitive information or giving them access to your accounts.
🔥 Real Example — Vishing Call
Your phone rings. The caller says:
“Hello, this is Amazon Fraud Department. We’ve detected suspicious activity on your account. To secure your account, please confirm your full name, address, and credit card number.”
Many people panic and start answering without thinking. Once attackers get this information, they use it for identity theft or financial fraud.
🚨 How to Spot Vishing
Listen carefully for these warning signs:
- 🟨 Caller ID spoofing: The number may appear as “Amazon”, “Your Bank”, or even “IRS.”
- 🟨 High-pressure tactics: Scammers often say “Act now, or your account will be locked.”
- 🟨 Requests for sensitive info: Remember — banks or legitimate companies never ask for your full password, PIN, or credit card number over the phone.
- 🟨 Fake background noise: You might hear fake call center sounds to make the call seem legitimate.
🧠 What Is a Phishing-Assumption Attack?
A phishing-assumption attack happens when attackers exploit something you are already expecting or thinking about.
For example:
- You recently ordered something from Amazon.
- Suddenly, you receive an email saying “Your Amazon delivery failed. Please update your address.”
- Because you’re genuinely waiting for a package, your brain lowers its defenses.
This psychological trick makes phishing attempts incredibly effective. Attackers succeed not because their message is convincing but because your brain fills in the gaps.
💣 What Can Go Wrong If You Fall for Phishing?
Phishing leads to:
- 🚨 Account theft: Hackers gain access to your email, social media, or bank accounts.
- 🚨 Identity theft: Scammers use your personal info to open credit lines or file fake tax returns.
- 🚨 Financial loss: Hackers drain your bank accounts or max out your credit cards.
- 🚨 Malware infections: Clicking malicious links can install spyware, ransomware, or trojans.
🔧 How to Detect and Defeat Phishing — Actionable Rules
✔️ Always check the sender or caller:
→ If something feels off, it probably is.
✔️ Hover over links before clicking (on desktop):
→ Check whether the URL matches the official website.
✔️ Scan for grammar errors, strange wording, or bad formatting.
✔️ Verify directly:
→ If your bank emails you, open the banking app — don’t click the link.
→ If Amazon calls, hang up and call them back using their official number.
✔️ Never give sensitive info like passwords, PINs, or 2FA codes via phone, SMS, or email.
✔️ Enable Two-Factor Authentication (2FA):
→ Even if attackers steal your password, 2FA blocks the login.
✔️ Use a password manager:
→ It won’t autofill on phishing sites since the domain won’t match.
🏴☠️ Real Data — How Common Is Phishing?
- 💥 3.4 billion phishing emails go out every day. (CISA, 2024)
- 💥 96% of phishing attacks arrive by email. (Verizon DBIR 2023)
- 💥 Smishing increased by 58% in 2023 alone.
- 💥 Vishing hit over 20,000 businesses in 2023. (FBI IC3 report)
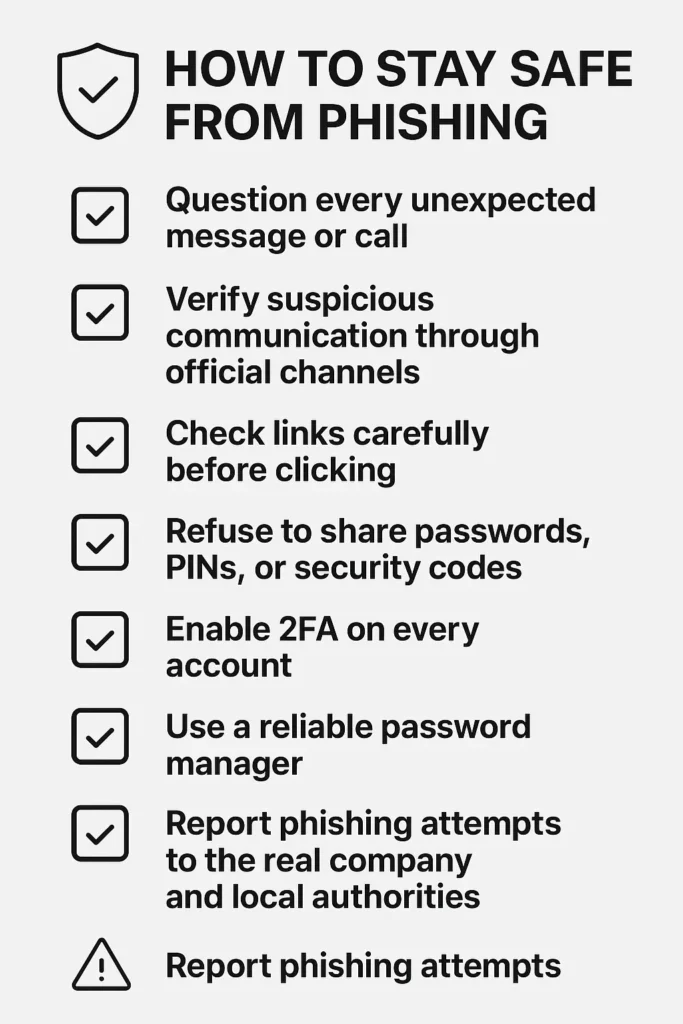
🚀 Checklist — How to Stay Safe From Phishing, Smishing, Vishing
- 🔲 Question every unexpected message or call
- 🔲 Verify suspicious communication through official channels
- 🔲 Check links carefully before clicking
- 🔲 Refuse to share passwords, PINs, or security codes
- 🔲 Enable 2FA on every account
- 🔲 Use a reliable password manager
- 🔲 Report phishing attempts to the real company and local authorities
🏆 Final Thoughts
Phishing works because hackers don’t attack computers — they attack people. They exploit urgency, fear, and your assumptions.
But now you’re better prepared. You know the signs, the tricks, and the defenses.
Remember: hackers don’t break locks. They trick you into unlocking the door. Stay alert. Stay secure.
✅ Final Note
Sources referenced:
- Verizon Data Breach Investigations Report (DBIR) 2023
- FBI IC3 Internet Crime Report 2023
- CISA Phishing Advisories (2024)
- OWASP Phishing Prevention Cheat Sheet
