🔐 Your Private Conversations Aren’t As Private As You Think — Here’s How to Fix That
Most people don’t realize when it happens.
There’s no alert. No camera flash. Just a moment — maybe days later — when something feels off. A password reset that wasn’t yours. A conversation that’s gone. A reply you never sent.
It doesn’t start with a breach. It starts with trust: the quiet assumption that the tools you use every day — your inbox, your messenger — are private by design. They aren’t. They’re private by habit. And habits are vulnerable.
While we obsess over encrypted apps and password vaults, attackers look for what we overlook: forwarded emails, dormant sessions, invisible access logs. They don’t need to break encryption if they can bypass it entirely. They don’t need your device — just your moment of distraction.
This guide is about the parts you don’t read in setup instructions. It’s about patterns, blind spots, and small oversights that lead to large consequences. It’s not a checklist — though we’ll give you one. It’s a shift in how you think about your conversations — not as casual exchanges, but as access points.
No fear. No panic. Just awareness — and control.
⚠️ Disclaimer
This article is written for educational and ethical purposes only. Its goal is to help readers secure their communication channels and protect their digital privacy.
🚨 Why Email and Messaging Security Matters More Than Ever
In 2025, your email is the master key to your entire digital life. If attackers gain access to your email, they can reset passwords, hijack accounts, drain your bank, and steal your identity. This is confirmed by the Verizon 2023 Data Breach Investigations Report (DBIR), which states that over 80% of hacking-related breaches involve stolen credentials.
Messaging apps are no different. Your conversations on WhatsApp, Telegram, Signal, and Messenger often contain financial data, private photos, login links, and sensitive information. A breach affects not only privacy but also your financial and professional life.
🏴☠️ How Hackers Attack Emails and Messengers
According to the FBI Internet Crime Complaint Center (IC3) 2023 report, cybercriminals most commonly use:
✔️ Phishing — tricking victims into handing over credentials via fake emails or websites.
✔️ Credential stuffing — using leaked passwords from previous data breaches.
✔️ SIM-swapping — hijacking phone numbers to intercept two-factor codes.
✔️ Malware and spyware — stealing session tokens and credentials.
✔️ Man-in-the-middle attacks (MITM) — intercepting traffic over unsecured networks.
✔️ Social engineering — manipulating support teams or individuals into resetting passwords.
🔐 How to Secure Your Email — Step by Step
1️⃣ Choose the Right Email Provider
The Cybersecurity and Infrastructure Security Agency (CISA) recommends selecting providers with strong security and encryption features.
✔️ Recommended secure email services:
- ProtonMail — encrypted, privacy-focused, based in Switzerland.
- Tutanota — fully encrypted and open-source.
- Gmail — strong security when configured correctly, though not privacy-first.
- Outlook — good enterprise security, less focused on privacy.
2️⃣ Enable Two-Factor Authentication (2FA)
CISA’s 2024 advisory explicitly warns that relying on passwords alone is insufficient. Enable 2FA using authenticator apps like Google Authenticator, Authy, or Microsoft Authenticator. Hardware-based 2FA, such as YubiKey or Google Titan, provides phishing-proof security.
3️⃣ Use a Strong, Unique Password
According to the NIST Digital Identity Guidelines (SP 800-63B), secure passwords should be at least 16 characters long and ideally use a passphrase model. Combine this with a password manager.
4️⃣ Check for Data Breaches
The nonprofit platform Have I Been Pwned, operated by cybersecurity expert Troy Hunt, allows users to check whether their email appeared in known data breaches. If found, change passwords immediately.
5️⃣ Set Up Backup Codes and Secure Recovery Options
CISA stresses that recovery options often become the weakest point. Backup codes must be stored securely (encrypted file, offline paper copy). Any secondary recovery email should also have 2FA enabled.
6️⃣ Lock Down Your Email Settings
The FBI IC3 report highlights how attackers use hidden forwarding rules to silently exfiltrate emails.
✔️ Check forwarding and filter settings.
✔️ Disable POP/IMAP if not needed.
✔️ Review recent login activity.
✔️ Enable login alerts.
7️⃣ Be Phishing-Proof
The Verizon DBIR 2023 confirms that phishing accounts for 36% of breaches involving social engineering.
→ Never click links in unsolicited emails.
→ Type URLs manually or use bookmarks.
→ Password managers help — they won’t autofill on phishing sites because the domain won’t match.
📱 How to Secure Your Messengers
1️⃣ Choose a Messenger with Strong Encryption
The Electronic Frontier Foundation (EFF) recommends messengers with end-to-end encryption (E2EE) enabled by default.
💬 Comparison of Major Messaging Apps (2025 Edition)
| 🛡 Feature / App | Signal | Telegram | iMessage | Facebook Messenger | |
|---|---|---|---|---|---|
| End-to-End Encryption (E2EE) | ✅ Always enabled (Open Whisper Protocol) | 🚫 Default: Cloud-based ✅ Secret Chats only | ✅ Default for all chats | ✅ iMessage only (not SMS) | 🚫 Only for secret conversations |
| Open Source | ✅ Fully open-source | 🟡 Partially (client only) | ❌ Closed-source | ❌ Closed-source | ❌ Closed-source |
| Metadata Protection | ✅ Strong — minimal data collected | ❌ Stores IP, contacts, and more | ❌ Collects metadata (e.g., who you talk to, when) | ❌ Tied to Apple ID and phone number | ❌ Extensive tracking and profiling |
| Message Disappearing / Timers | ✅ Customizable auto-delete | ✅ Available in secret chats | ✅ Optional disappearing messages | ✅ Optional for messages | ✅ Limited disappearing messages |
| Multi-Device Support | ✅ Yes (full sync, no phone required) | ✅ Yes (via cloud) | ✅ Yes (but tied to phone number) | 🟡 Yes, but Apple-only ecosystem | ✅ Yes (cloud sync) |
| Account Tied to Phone Number | ✅ But plans to remove this | ✅ Yes | ✅ Yes | ✅ Yes | ✅ Yes |
| Backup Encryption | ✅ Local and encrypted | ❌ Cloud-based, not E2EE | 🟡 Google Drive/iCloud (opt-in, now encrypted) | ✅ iCloud encrypted (recent update) | ❌ Backups not E2EE |
| Ownership | Nonprofit (Signal Foundation) | Private (Durov brothers) | Meta (Facebook) | Apple | Meta (Facebook) |
| Business Model | Donations | Ads coming for channels | Meta ecosystem (data) | Hardware sales | Data monetization |
| Ads / Data Mining | ❌ No ads, no tracking | 🟡 Minimal (for now) | ✅ Data shared with Meta | ❌ No ads | ✅ Extensive profiling |
| Ideal Use Case | Maximum privacy, activists | Public channels, flexibility | Mass usage, family & friends | Apple users only | Facebook users, casual chats |
2️⃣ Enable Two-Step Verification (2FA) on Messengers
FBI IC3 2023 highlights that enabling PIN codes or two-step verification in messengers blocks most SIM-swap-based hijacks.
3️⃣ Secure Your SIM Card
SIM-swapping caused over $72 million in losses in 2023 (FBI IC3 report). Call your carrier to:
✔️ Enable SIM Lock with a PIN.
✔️ Activate Port-Out Protection or Number Lock.
4️⃣ Lock Messenger Apps with Biometrics or PIN
A 2023 case study from KrebsOnSecurity demonstrates that even if someone steals your phone, having biometric locks on apps like WhatsApp or Telegram prevents attackers from accessing chat history.
5️⃣ Handle Backups Carefully
WhatsApp’s FAQ admits that cloud backups on Google Drive or iCloud are not encrypted by default. However, since late 2022, they added the option for end-to-end encrypted backups.
✔️ Go to Settings → Chats → Chat Backup → End-to-End Encrypted Backup → Turn On.
Telegram’s cloud chats are NOT end-to-end encrypted. Only Secret Chats are fully encrypted.
6️⃣ Watch Out for Phishing Links in Chats
The FBI IC3 and CISA phishing advisories (2024) both note a rise in phishing attempts delivered via messenger apps.
→ Treat suspicious links in WhatsApp, Telegram, or Signal the same way you treat phishing emails.
→ Verify senders through a separate channel if needed.
7️⃣ Disable Notification Previews on Lock Screen
According to the EFF Privacy Guide, notifications on a locked screen expose sensitive content to anyone nearby. Disable previews to prevent data leaks if your phone is stolen.
8️⃣ Check for Active Sessions and Devices
WhatsApp Web, Telegram Web, and other messengers allow remote logins. Regularly check for unknown active sessions.
✔️ WhatsApp: Settings → Linked Devices
✔️ Telegram: Settings → Devices
🏴☠️ Real-World Example — The Cost of Poor Email Security
In 2023, a small law firm in California lost $244,000 due to a simple email compromise. The FBI IC3 case report shows how attackers gained access to a paralegal’s Gmail via a phishing email. They created hidden forwarding rules to monitor all communication unnoticed.
When the firm initiated a real estate transaction, the attackers impersonated the client and redirected the payment. The firm discovered the fraud only after the money disappeared.
Lesson: Email is not just your inbox — it’s your master key. Lose it, and you risk losing everything.
🚀 Pro Tips — Next-Level Protection
✔️ Use privacy-focused browsers like Brave or Firefox.
✔️ Install security extensions: uBlock Origin, Privacy Badger, HTTPS Everywhere.
✔️ Use a VPN on public Wi-Fi to prevent MITM attacks (CISA recommends this for remote workers.)
✔️ Use a hardware key (YubiKey, Titan) for email and cloud services.
✔️ Store credentials in a password manager with 2FA.
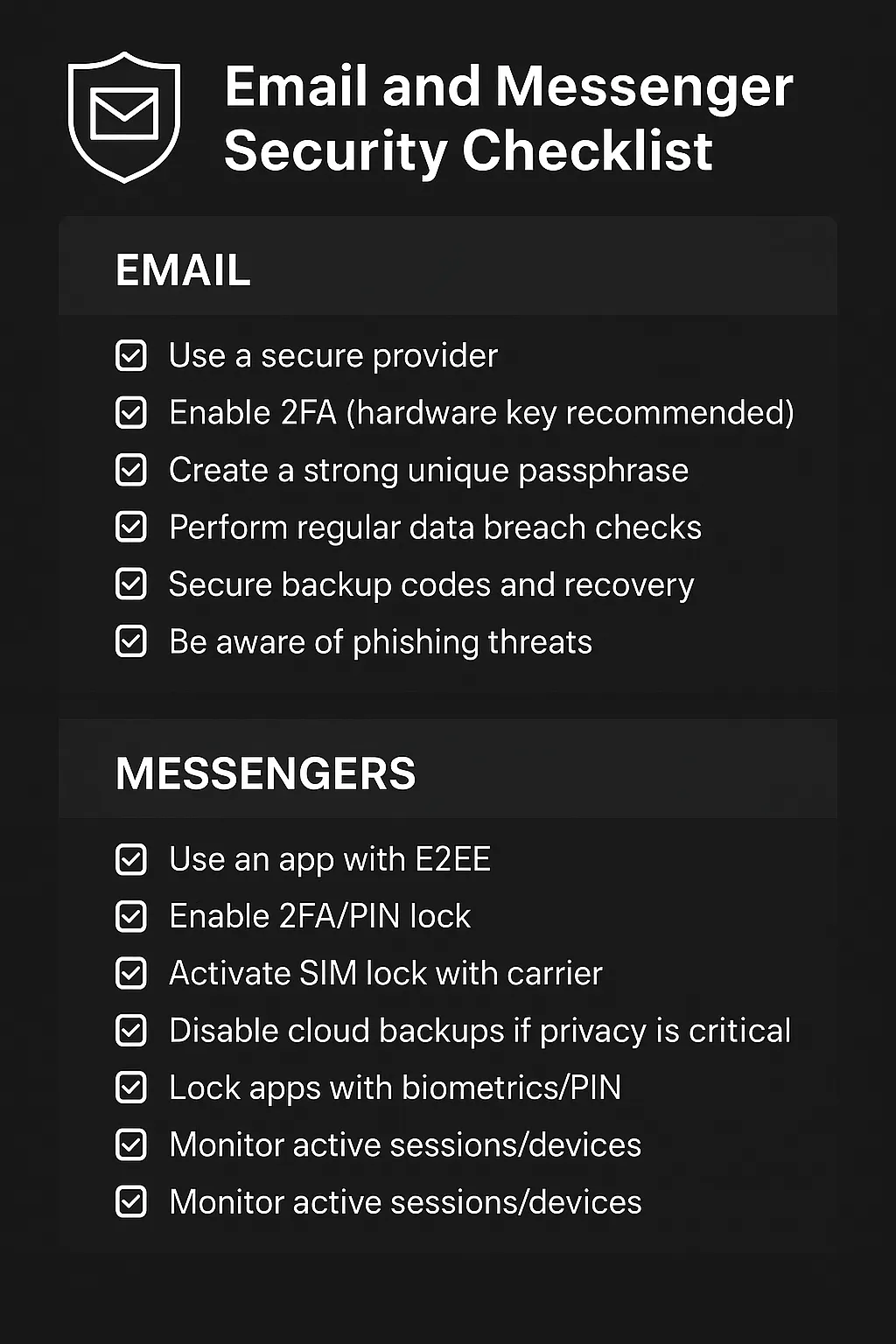
📊 Checklist — Email and Messenger Security
📧 Email:
- 🔲 Secure provider with proper settings)
- 🔲 2FA enabled (hardware key preferred)
- 🔲 Strong unique passphrase
- 🔲 Regular data breach checks
- 🔲 Secure backup codes and recovery
- 🔲 Check filters, forwards, login history
- 🔲 Be phishing-aware
📲 Messengers:
- 🔲 Use Apps with E2EE
- 🔲 2FA/PIN lock enabled
- 🔲 SIM lock activated with carrier
- 🔲 Disable cloud backups if privacy is critical
- 🔲 Lock apps with biometrics/PIN
- 🔲 Disable lock screen previews
- 🔲 Monitor active sessions/devices
🏆 Final Thoughts
The FBI, CISA, OWASP, and Verizon agree on one thing: email and messengers are prime targets for attackers. Your inbox isn’t just a mailbox — it’s your key to everything.
→ Hackers don’t break into accounts. They trick you into opening the door. With this guide, you now know how to keep that door firmly shut.
✅ Final Note
Sources referenced directly inside the article:
- Verizon Data Breach Investigations Report (DBIR) 2023
- FBI Internet Crime Complaint Center (IC3) Report 2023
- CISA Secure Email and Phishing Advisory 2024
- NIST Digital Identity Guidelines (SP 800-63B)
- EFF Privacy and Security Guides
- Signal, WhatsApp, Telegram, Gmail official documentation
- KrebsOnSecurity case reports
