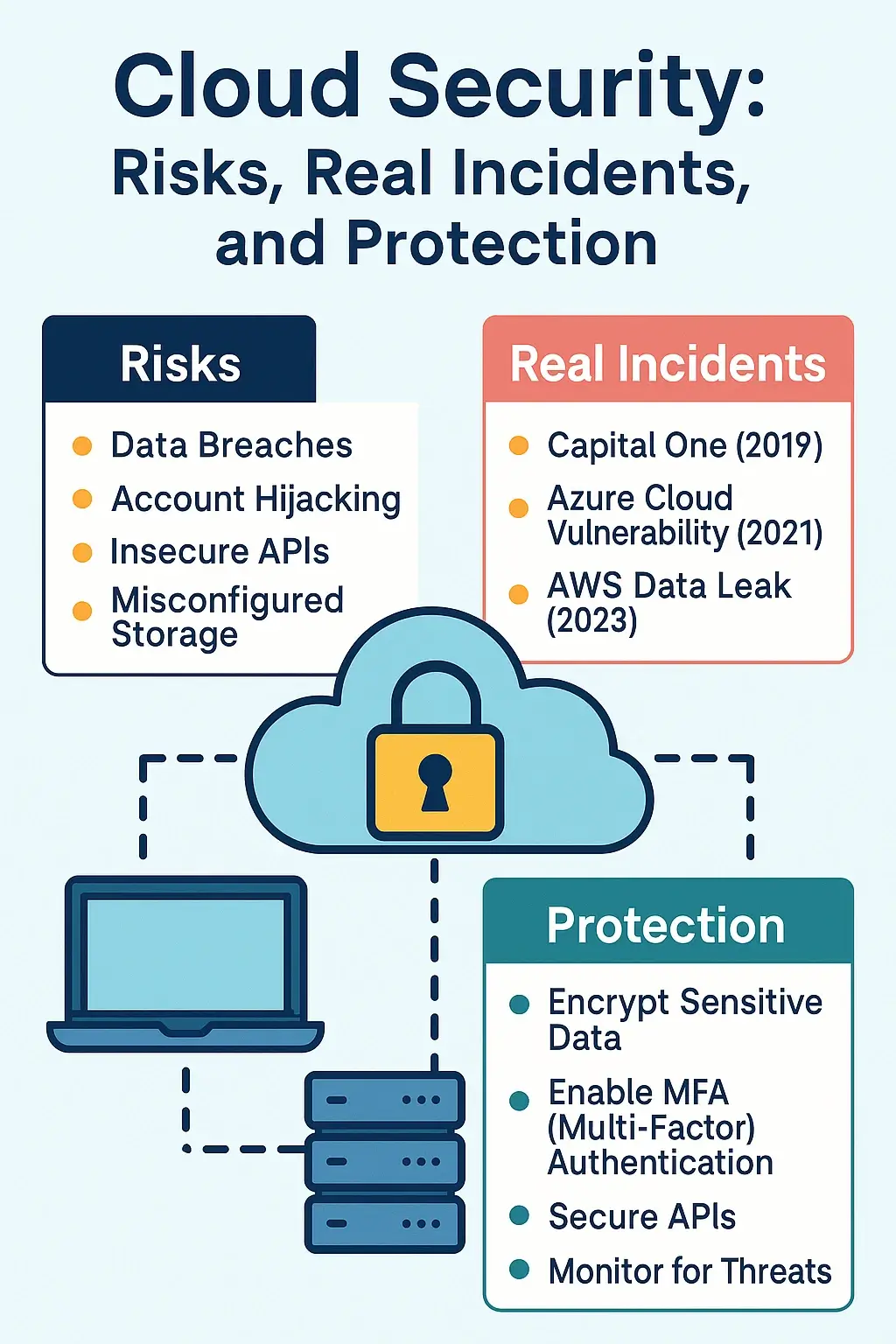
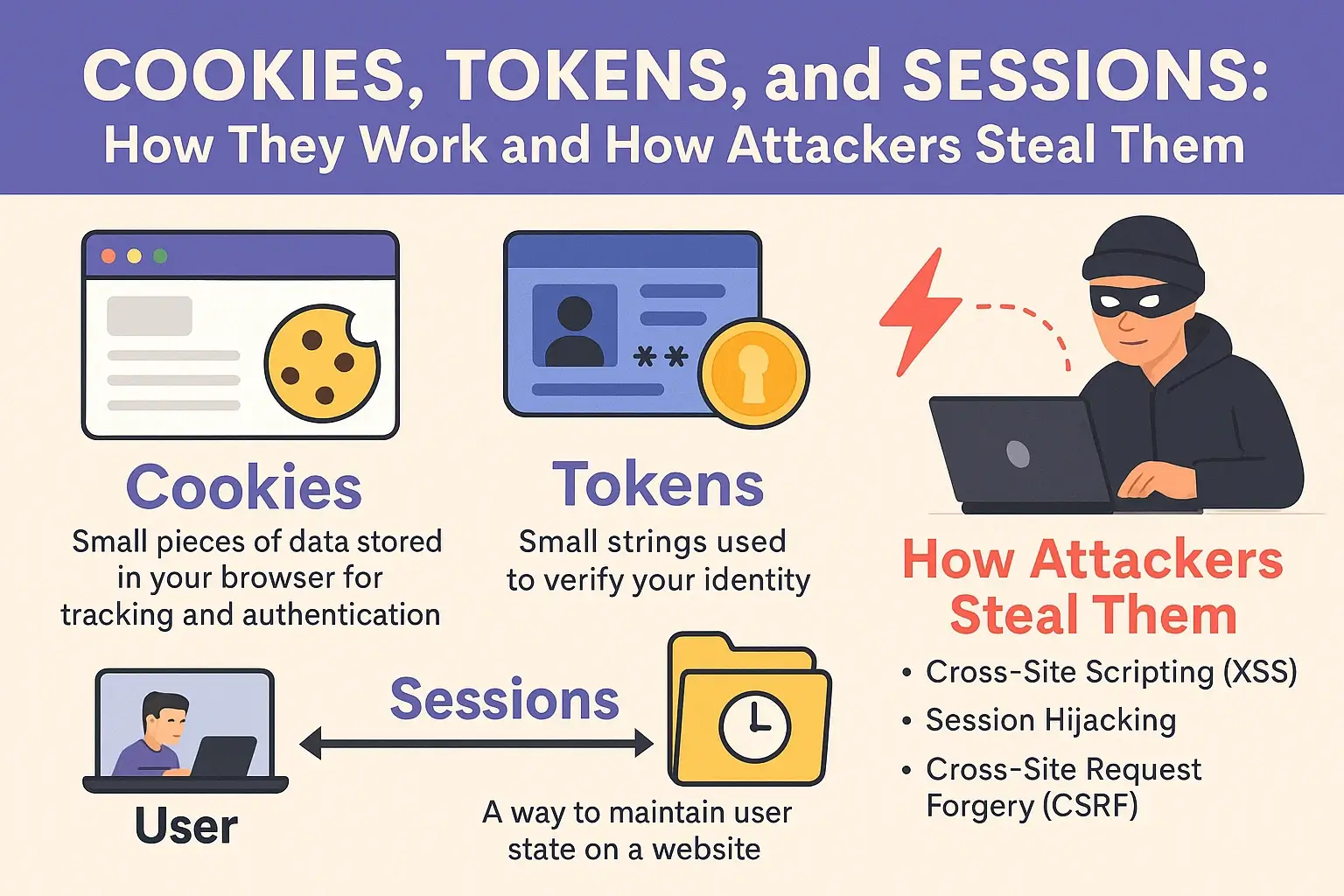
☁️ Cloud Security: Real Risks and How to Protect Your Data
Last Updated: July 2025 ⚠️ Disclaimer This article is written for educational and ethical purposes only. Its goal is to help readers understand cloud security risks and learn best practices to prevent data breaches and unauthorized access. 🔍 Introduction The shift to cloud computing has transformed how individuals and businesses store, access, and manage data. … Read more