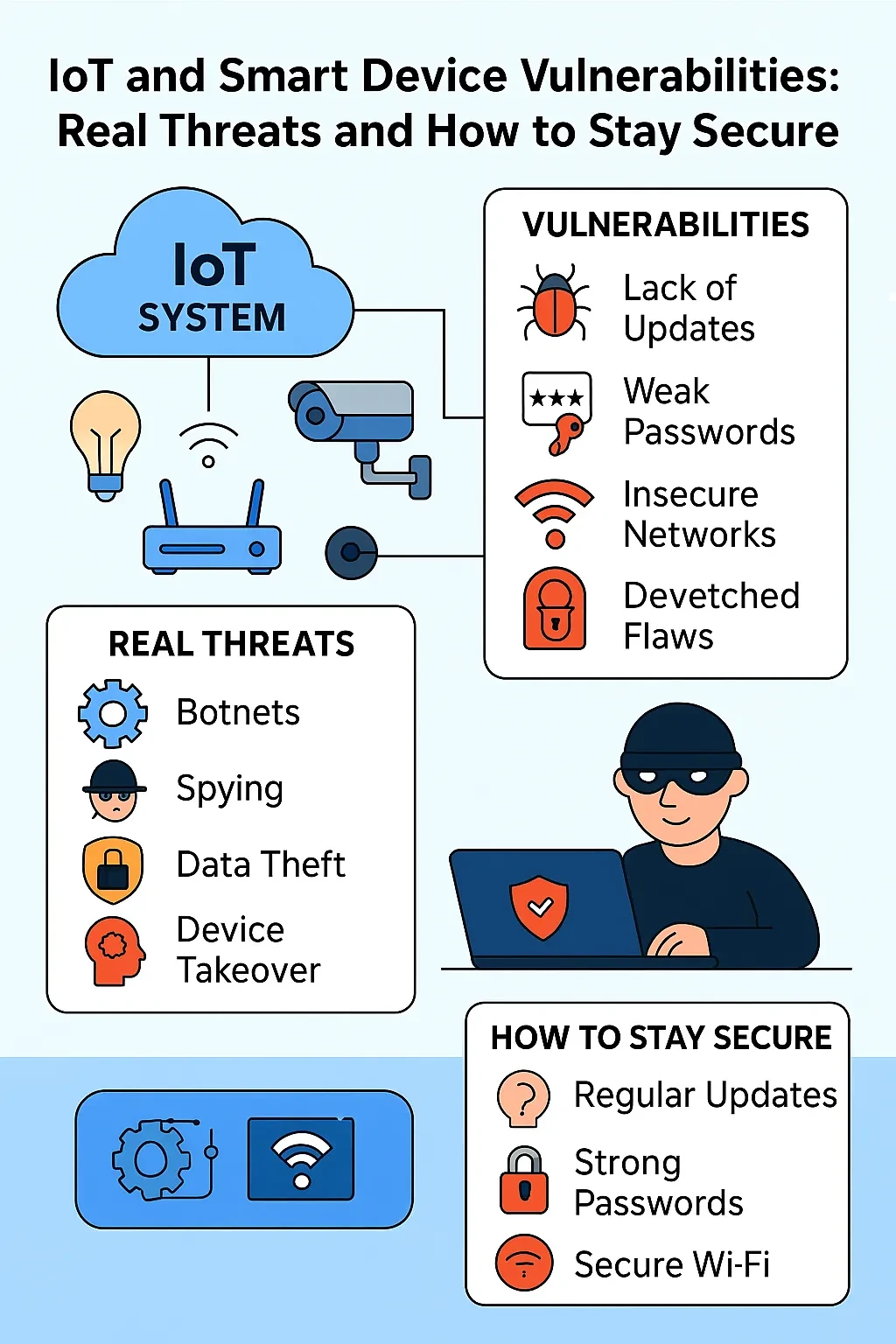
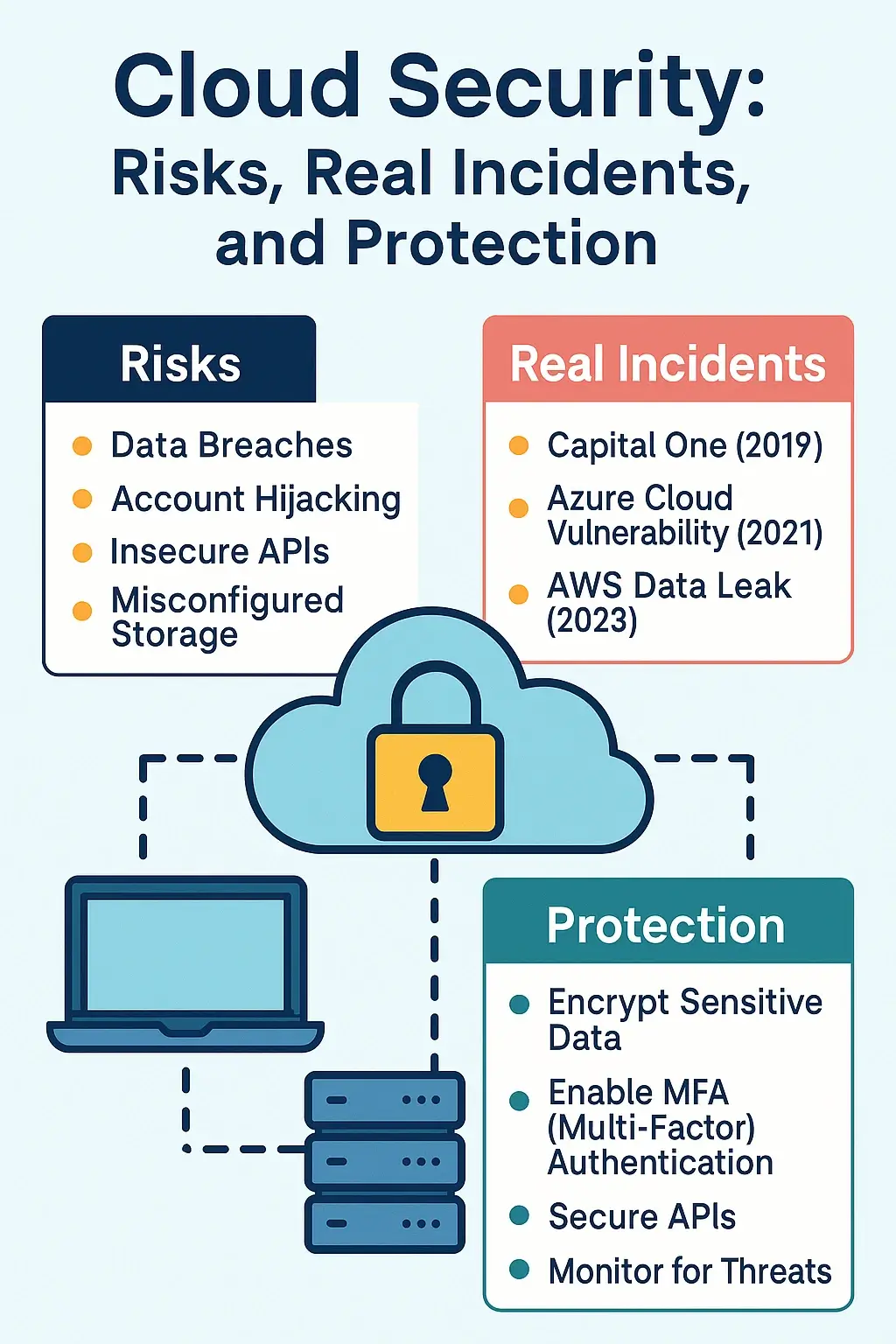
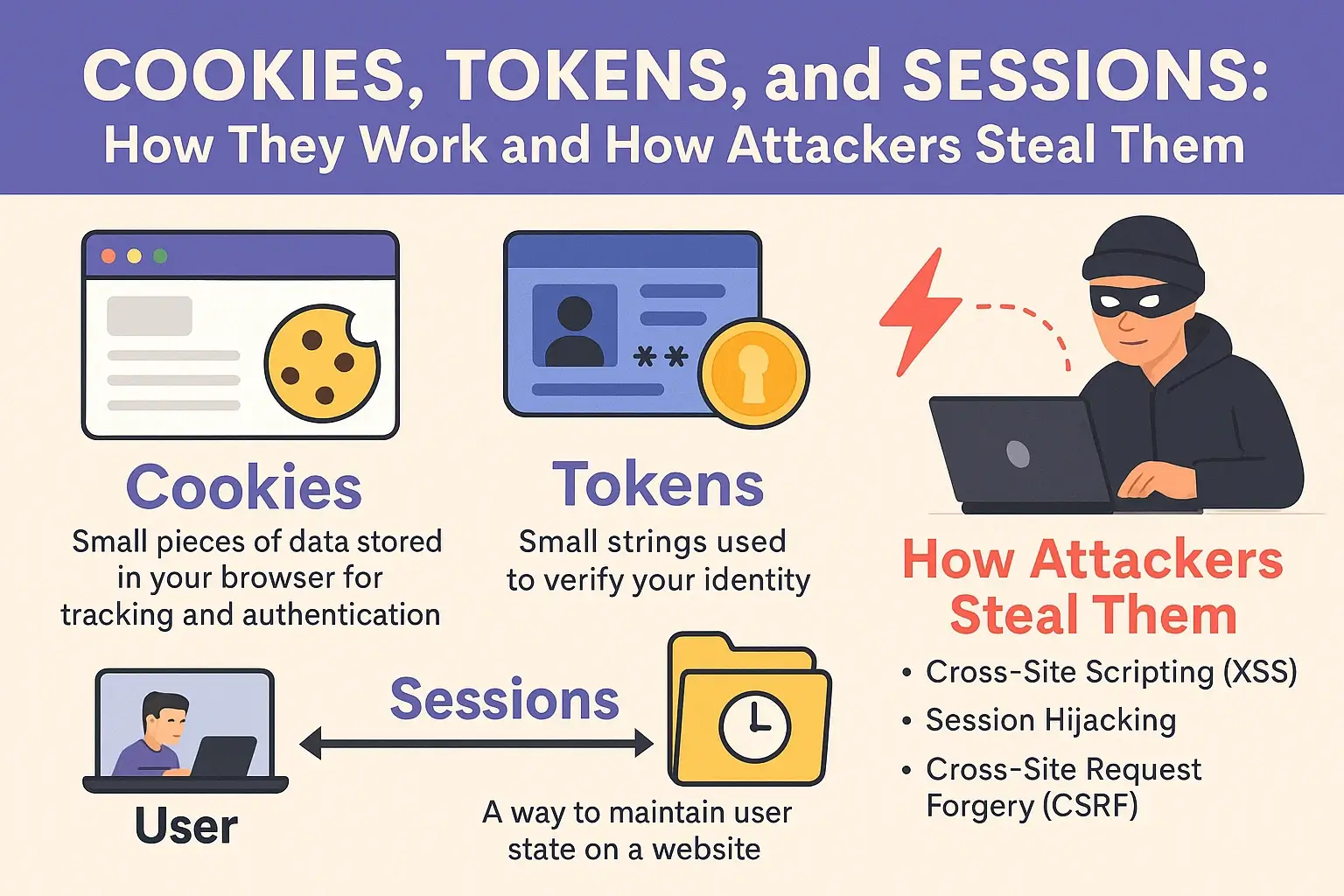
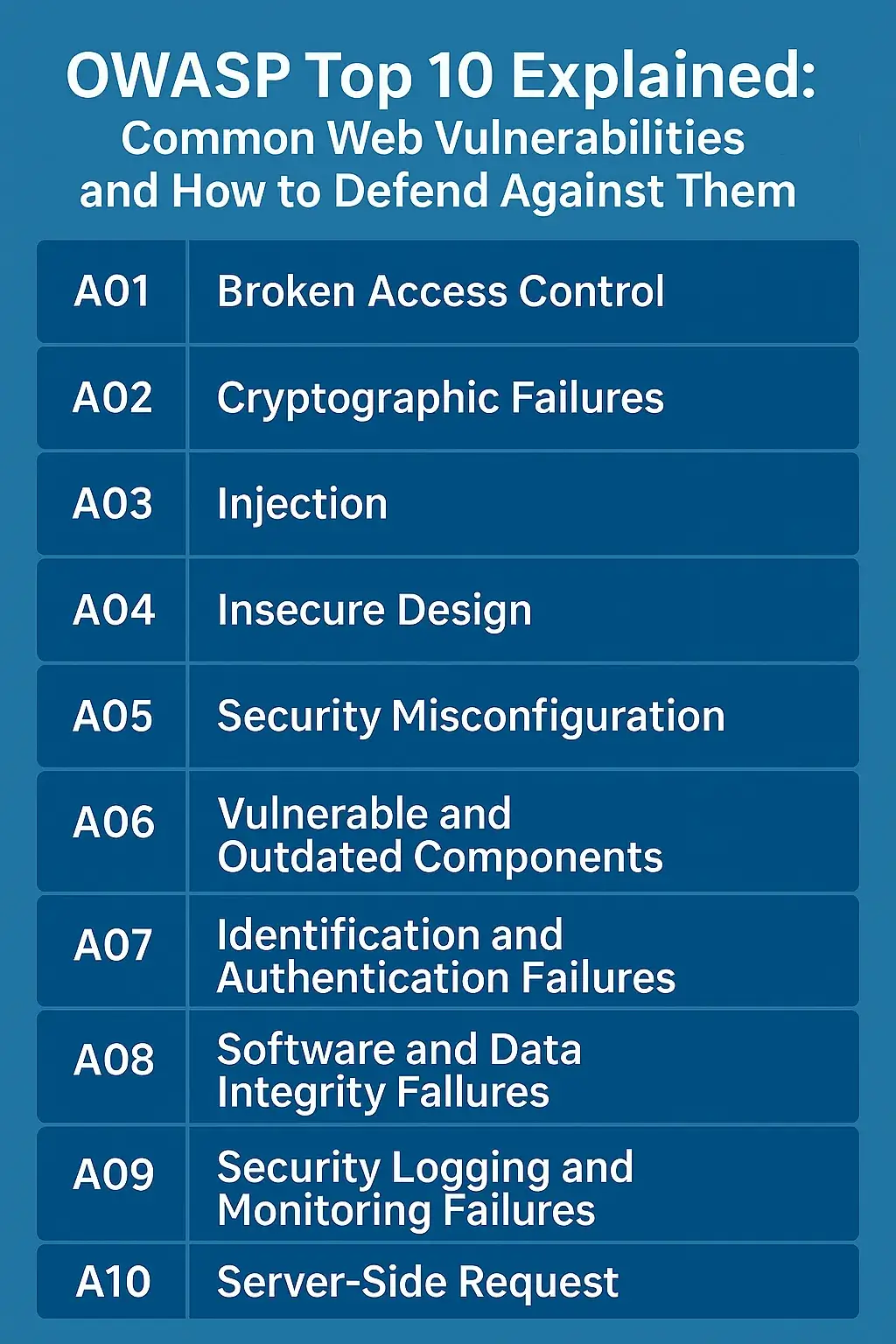
📡 IoT and Smart Device Vulnerabilities: Real Threats and How to Stay Secure
🧠 Introduction The Internet of Things (IoT) is revolutionizing how we live — from smart thermostats and connected doorbells to industrial sensors and medical implants. However, this connectivity also introduces new security challenges. Many IoT devices lack robust security features, making them attractive targets for cybercriminals. ⚠️ Disclaimer This article is written for educational and … Read more