Ports and Protocols: TCP/UDP — How Hackers and Defenders Use Them
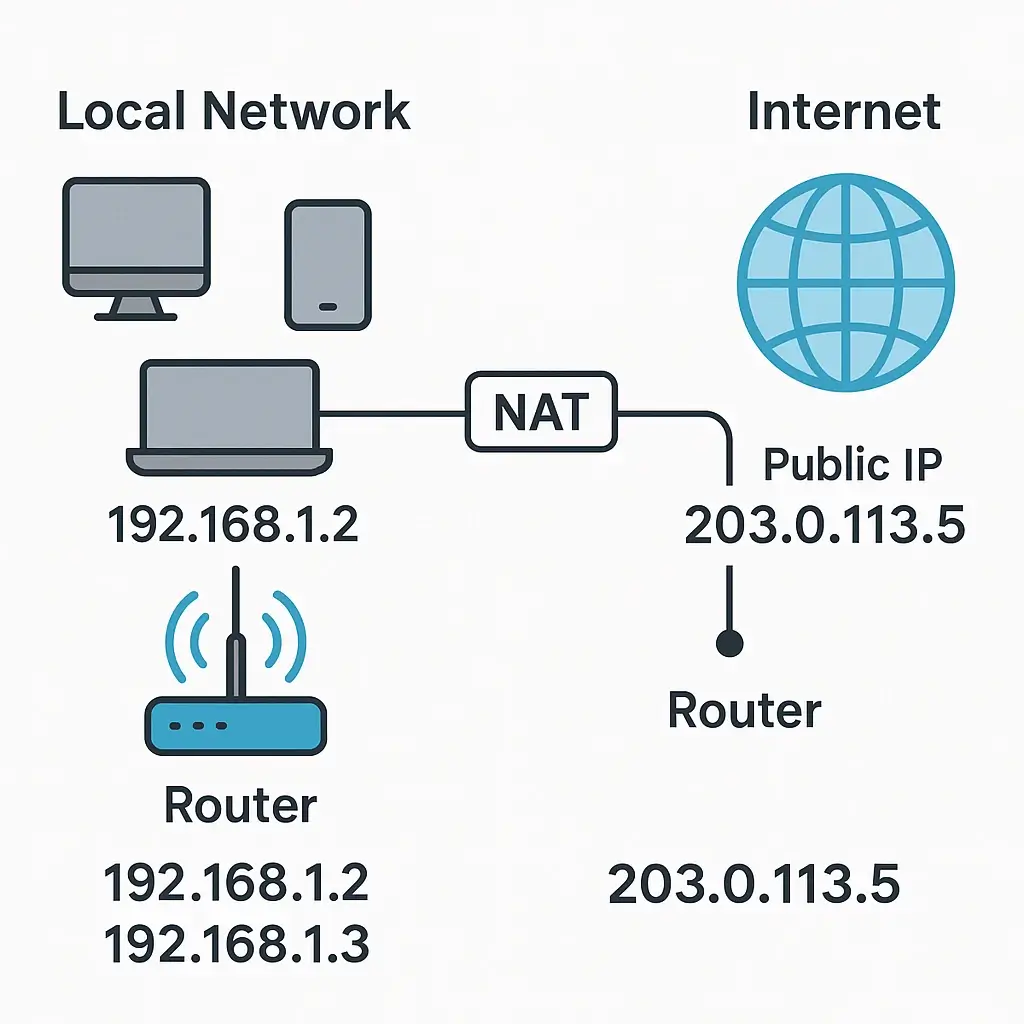
🧠 Understanding Ports Is Critical for Cybersecurity. ⚠️ Disclaimer This article is written for educational and ethical purposes only. Its goal is to help readers understand how TCP/UDP ports and protocols work, how they are used in both cyberattacks and cybersecurity defense. 🚩 What Are Ports in Networking? A port is a virtual door on … Read more