⚠️ Disclaimer
This article is for educational purposes only. It does not promote or endorse illegal activities. All content complies with international cybersecurity and legal standards.
🔍 Introduction — The Attack That Doesn’t Need to Hack You
Some of the most dangerous cyberattacks don’t exploit zero-day vulnerabilities or deploy sophisticated malware. They simply log in.
Credential stuffing works exactly like that: criminals take a username and password stolen from one site, then use automated tools to try the same combo on dozens, hundreds, or even thousands of other websites.
If you’ve ever reused a password — and studies show 65% of people still do — you’ve made the attacker’s job effortless.
The results? Compromised emails, drained bank accounts, hijacked Netflix subscriptions, and even full identity theft — all without a single “Hollywood-style” hack.
🧩 How Credential Stuffing Works — Step by Step
| Step | What Happens | Tools Criminals Use | Real-World Analogy |
|---|---|---|---|
| 1 | Data Breach — passwords are stolen from one site. | Phishing kits, database leaks | A thief steals one master key from a gym locker room. |
| 2 | Credentials Are Sold or Shared on the dark web. | Dark web forums, Telegram channels | That key is now sold at a shady market. |
| 3 | Automated Attacks Begin — bots test the same combo elsewhere. | Special software | A robot tries the key on every locker in the city. |
| 4 | Successful Logins Lead to Takeover | Proxy networks, credential lists | One locker opens — everything inside is stolen. |
| 5 | Monetization — stolen accounts are used or sold. | Account marketplaces | They rent or sell the locker to someone else. |
📊 Why Credential Stuffing Works in 2025
This attack thrives because of three unstoppable trends:
- Password Reuse Epidemic — The same credentials protect banking, email, shopping, and entertainment accounts.
- Relentless Breach Volume — Billions of passwords leak every year. In 2024 alone, over 8 billion credentials were exposed (SpyCloud).
- Cheap Automation — Credential stuffing kits cost less than a cup of coffee and require zero coding skills.
🔐 The 2025 Ultimate Defense Playbook
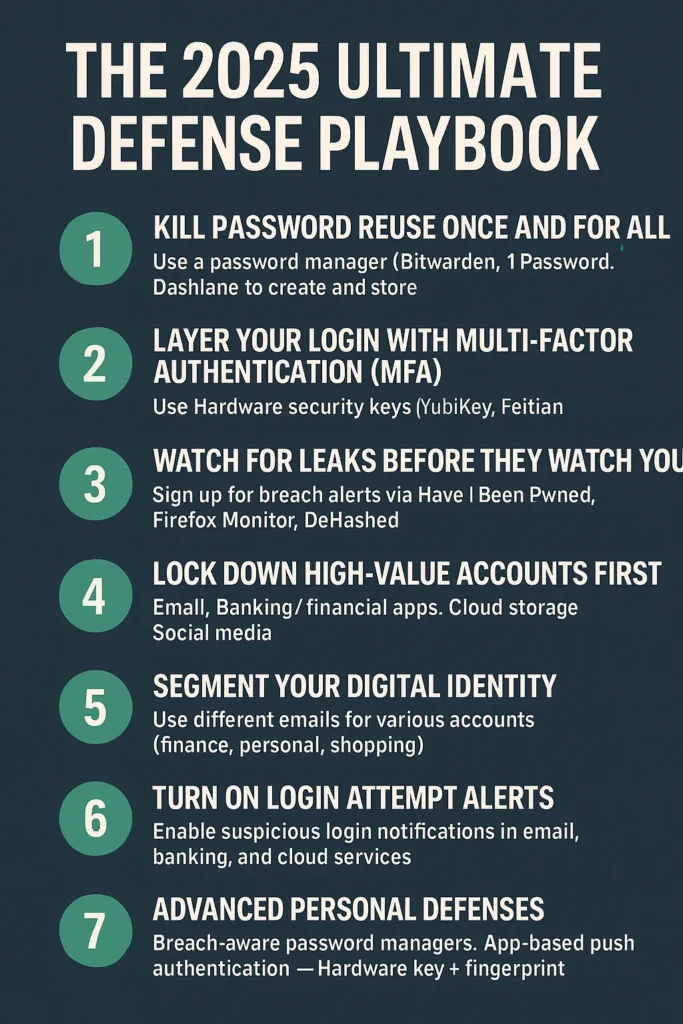
1️⃣ Kill Password Reuse Once and for All
- Use a password manager (Bitwarden, 1Password, Dashlane) to create and store unique logins for every account.
- For critical accounts, use passphrases — longer, more memorable combinations of words that are far harder to brute-force.
2️⃣ Layer Your Login with Multi-Factor Authentication (MFA)
- Even if a password leaks, MFA stops attackers cold.
- Best in 2025: Hardware security keys (YubiKey, Feitian), ideally with biometric verification.
- Avoid: SMS codes where possible — they can be hijacked through SIM-swapping.
3️⃣ Watch for Leaks Before They Watch You
- Sign up for breach alerts via Have I Been Pwned, Firefox Monitor, or DeHashed.
- Enable browser-level password breach detection in Chrome, Firefox, or Safari.
4️⃣ Lock Down High-Value Accounts First
Prioritize accounts that can reset others:
- Banking / financial apps
- Cloud storage
- Social media
5️⃣ Segment Your Digital Identity
- Use different emails for different account types (finance, personal, shopping).
- Keep low-security accounts separate from your primary email.
6️⃣ Turn On Login Attempt Alerts
- Enable suspicious login notifications in email, banking, and cloud services.
- Consider geo-fencing logins so accounts can only be accessed from your home country.
7️⃣ Advanced Personal Defenses
- Breach-aware password managers (e.g., 1Password Watchtower) automatically check for leaked credentials.
- App-based push authentication (Authy, Duo) to approve logins from your phone — not just codes.
- Hardware key + fingerprint for mission-critical accounts.
🕵️ How to Spot Credential Stuffing in Action — Before It’s Too Late
Even the strongest security setup works better if you can spot an attack early. Credential stuffing leaves distinct patterns — both for individuals and organizations.
For Individuals
- Unfamiliar Login Alerts — Emails or app notifications about logins from devices or locations you don’t recognize.
- Password Reset Emails You Didn’t Request — A clear signal someone is trying to take over your account.
- Sudden Account Lockouts — Multiple failed login attempts triggering a security block.
- Strange Activity in Your Accounts — New streaming profiles, unexpected charges, or unfamiliar files appearing in cloud storage.
For Businesses
- Login Spikes at Odd Hours — Unusual surges in failed logins, often in early morning hours.
- Multiple Accounts Accessed from the Same IP — Indicative of automated bot attacks.
- Geographic Anomalies — Many logins from countries outside your customer base.
- High MFA Failure Rates — Bots hitting accounts with MFA enabled, failing at the second step.
Tip: If you detect these warning signs, act immediately — change passwords, lock compromised accounts, and review system logs for wider breaches.
🛡️ Corporate & Developer Defenses (2025 Best Practices)
Credential stuffing can overwhelm customer accounts and damage brand trust. Modern countermeasures include:
- Rate Limiting: Restrict login attempts per IP or per account.
- Bot Detection: Deploy Cloudflare Bot Management or reCAPTCHA Enterprise.
- Credential Hash Checks: Block known leaked credentials via the Have I Been Pwned API.
- Device Fingerprinting: Detect abnormal login patterns based on browser, OS, and device ID.
- Adaptive MFA: Trigger MFA only for risky logins to keep user friction low.
- Honeypot Accounts: Plant fake credentials to detect automated abuse.
- Impossible Travel Detection: Flag logins from two distant countries in an unrealistically short time.
💡 Quick Self-Check: Are You Vulnerable?
You’re at risk if you answer YES to any of these:
- You reuse passwords.
- You haven’t changed your main email password in 12+ months.
- You still use SMS for MFA.
- You’ve never checked a breach database for your email.
📖 Glossary
- Credential Stuffing — Using stolen usernames/passwords from one service to log in to another.
- Passphrase — A longer password made from multiple words, harder to crack.
- Multi-Factor Authentication (MFA) — Adding a second verification step to a login process.
- SIM-Swapping — Fraud where criminals take control of your phone number to bypass SMS-based security.
❓ FAQ
Q: Is credential stuffing the same as brute force?
A: No. Brute force tries random passwords. Credential stuffing uses known, leaked credentials.
Q: What if I already reused passwords?
A: Change them immediately, starting with your email.
Q: Are password managers safe?
A: When used properly, yes — they’re safer than storing passwords in browsers or memory.
🏁 Conclusion — The Easiest Attack to Stop
Credential stuffing is an attack on habits, not hardware.
In 2025, billions of stolen credentials are circulating, but you can remove the attacker’s “master key” entirely:
- Stop password reuse.
- Enable MFA.
- Monitor your accounts.
The next breach is already happening somewhere — make sure your credentials aren’t the ones being tested tonight.
