⚠️ Disclaimer
This article is for educational and awareness purposes only. It does not promote unauthorized access, malware deployment, or any illegal activities. All content complies with international cybersecurity and legal standards.
🧠 Introduction: The Gold Rush You Never Signed Up For
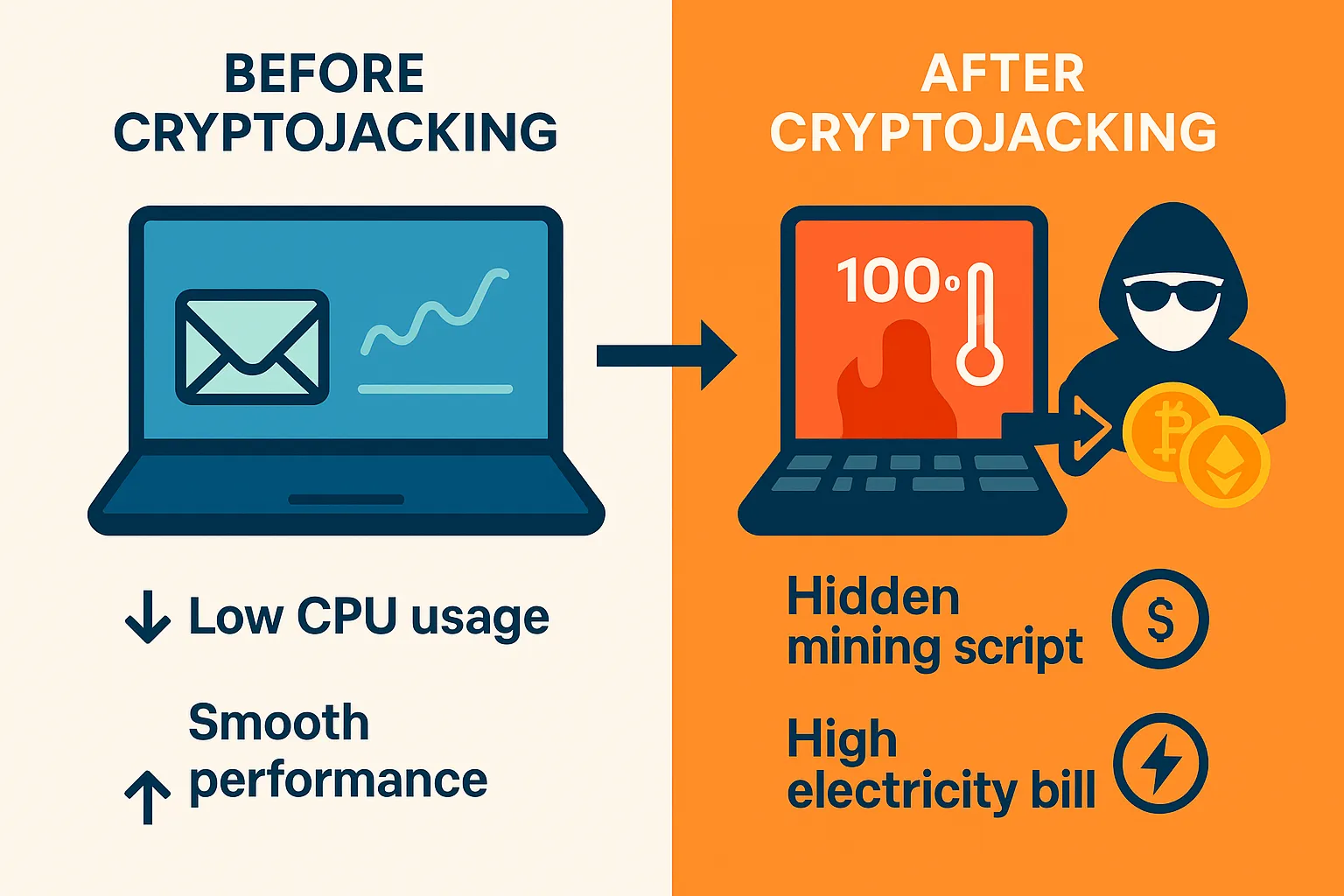
Your fans are spinning. Your laptop is overheating. Your battery dies faster than it should. You think it’s Chrome or maybe that new video editor. But the truth might be darker — and more profitable — than you imagine.
You’re not just using your computer. Someone else is, too.
Not for stealing your passwords. Not for locking your files.
But for something far more subtle.
They’re mining cryptocurrency — on your machine, using your electricity, right under your nose.
You didn’t agree to donate your CPU. You didn’t click “I accept” to fund a stranger’s crypto wallet. Yet here you are — paying the price for someone else’s profit.
Welcome to cryptojacking — the digital equivalent of someone sneaking into your house and plugging their mining rig into your power outlet.
💣 What Is Cryptojacking?
Cryptojacking is the unauthorized use of someone’s device — computer, phone, or even IoT gadget — to mine cryptocurrency. Instead of breaking into your bank, hackers hijack your CPU or GPU to generate coins like Monero, using your electricity and computing power while you pay the bill.
Unlike ransomware, cryptojacking doesn’t demand anything upfront. That’s its genius. It operates quietly, focusing on stealth over destruction — a parasite, not a predator.
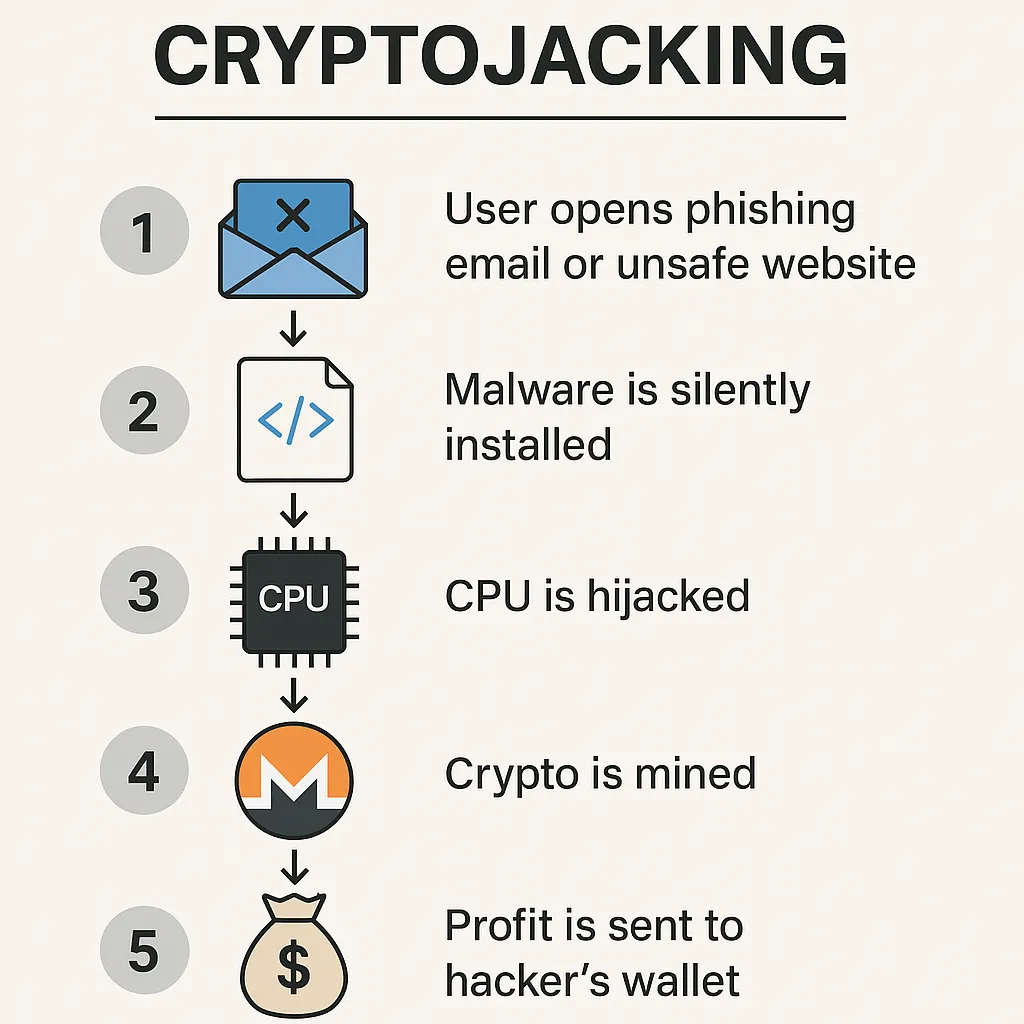
🔍 How It Works: From Code to Coin
Cryptojacking usually happens in one of two ways:
1. Malware-Based
You click a link, download a file, or open an attachment. Malware gets installed silently. It runs in the background, often disguised as a legitimate system process (like svchost.exe or explorer.exe). No ransom note, no obvious breach — just a spike in your CPU usage.
2. Browser-Based (Drive-By Mining)
You visit a website. Without downloading anything, JavaScript embedded in the page starts mining cryptocurrency. Close the tab, and the mining usually stops — unless the script runs in a hidden window.
Imagine you’re watching a YouTube video. It lags. Your fan starts humming like a jet engine. But you’re not running anything heavy. What you don’t see — is a mining script quietly milking your CPU in the background.
Popular tools like Coinhive (now defunct) once made it easy for websites to profit via visitors’ CPU cycles. The idea wasn’t always malicious — but the execution often was.
📉 Why It’s Dangerous
Cryptojacking might sound “better” than data theft. But make no mistake:
- It shortens hardware lifespan by running devices at full throttle.
- It drains mobile batteries, causing rapid wear.
- It raises electric bills, especially in corporate environments.
- It opens doors to further malware infections.
- It slows performance, impacting business and productivity.
And perhaps worst of all: It’s hard to notice. Most users discover cryptojacking weeks or months after infection, usually through abnormal behavior or IT audits.
🏢 Business Risk Snapshot
In corporate environments, cryptojacking can:
- Spike cloud bills (especially on AWS, Azure, or GCP)
- Cause premature server hardware failure
- Hide inside containerized apps or dev tools
- Waste thousands in energy costs monthly
🧾 In 2020, some enterprises reported losses exceeding $100,000 per incident — not from theft, but from silence.
🧑💻 Real Cases
💼 Tesla (2018)
Hackers breached Tesla’s Kubernetes admin console (no password set) and ran cryptomining scripts on Amazon Web Services (AWS). They used stealthy tactics: hiding mining traffic behind Cloudflare and limiting CPU usage to avoid detection.
📚 Government Websites (2018)
Over 4,000 government sites — including the UK’s Information Commissioner’s Office — were found running Coinhive mining scripts via a compromised accessibility plugin.
📱 Android Phones (2017–2019)
Apps disguised as games or utilities (e.g., wallpaper changers) included hidden miners. Some even bricked devices by overloading their processors.
🛡️ How to Detect Cryptojacking
| 🔍 Sign | 🧠 What It Means |
|---|---|
| CPU constantly maxed out | Mining tasks are running in the background |
| Overheating or loud fans | Devices pushed to their limit |
| Short battery life | High resource usage on mobile devices |
| Laggy performance | Browser or apps freeze or slow down |
| Suspicious browser behavior | Tabs that don’t close or reload automatically |
🧠 Pro tip: Use Task Manager (Windows) or Activity Monitor (Mac) to check unknown high-usage processes. On Linux, use htop.
🧰 How to Protect Yourself
| 🛠️ Action | ✅ Why It Helps |
|---|---|
| Use reputable antivirus software | Detects and removes mining malware |
| Install browser mining blockers | Extensions like uBlock Origin or No Coin |
| Keep software updated | Patches known vulnerabilities |
| Disable JavaScript on shady sites | Prevents drive-by mining scripts |
| Monitor CPU/GPU behavior | Unusual spikes are red flags |
| Train staff | Corporate infections often start with phishing |
🏢 Business environments should also implement firewall rules, endpoint detection, and regular audits.
📘 Glossary
- Cryptojacking: Unauthorized mining of cryptocurrency using someone else’s device.
- Coinhive: A now-defunct JavaScript mining service often abused by hackers.
- Drive-By Mining: Cryptomining that runs via web browser scripts, without installing software.
- Monero (XMR): A privacy-focused cryptocurrency, commonly mined in cryptojacking due to its CPU-friendly algorithm.
- Obfuscated Code: Code that’s deliberately made hard to read — used to hide malicious behavior.
❓FAQ
Q: Is cryptojacking illegal?
A: Yes. Unauthorized use of computing resources for mining is considered cybercrime in most jurisdictions.
Q: Why do attackers prefer Monero?
A: Because it’s private, hard to trace, and doesn’t require powerful GPUs — just a hijacked CPU.
Q: Can websites mine crypto with my permission?
A: Technically yes, but it’s rare. Most cases involve hidden scripts without user consent.
Q: How much money can hackers make?
A: One infected machine might earn a few cents per day. But scale it to thousands, and it becomes profitable.
🚨 Final Thoughts: The Hidden Tax of the Digital Age
Cryptojacking isn’t flashy. It doesn’t lock your files or drain your bank account. But it steals something more insidious — your time, your power, and your trust in technology.
It’s a crime that thrives in silence.
And that silence is your signal to start listening.
Before you close this tab, take a second to open your Task Manager. Look for anything strange. Then install a browser mining blocker like uBlock Origin.
Your CPU will thank you — and your electricity bill too.
