🧠 What Is a Hash Function?
A hash function is a mathematical algorithm that takes input data of any size and produces a fixed-size string of characters — the hash value, often called a digest or checksum.
✔️ Hashing is one-way encryption. Unlike regular encryption, hashes cannot be reversed to recover the original data (in theory).
🔥 What Makes a Good Hash Function:
- Deterministic: Same input always produces the same output.
- Fast: Quickly generates the hash value.
- Irreversible: Cannot convert the hash back to the original data.
- Collision-Resistant: No two different inputs should produce the same hash.
- Avalanche Effect: A small change in input produces a drastically different output.
💼 What Are Hash Functions Used For?
✔️ Common Use Cases:
- Password storage: Passwords are hashed before being saved to a database.
- Data integrity: Verify if files or messages were altered (checksums).
- Digital signatures: Hashes are used in creating and verifying signatures.
- Blockchain: Cryptocurrencies like Bitcoin depend on hashing for integrity.
- Certificate verification: SSL/TLS certificates use hash functions to validate authenticity.
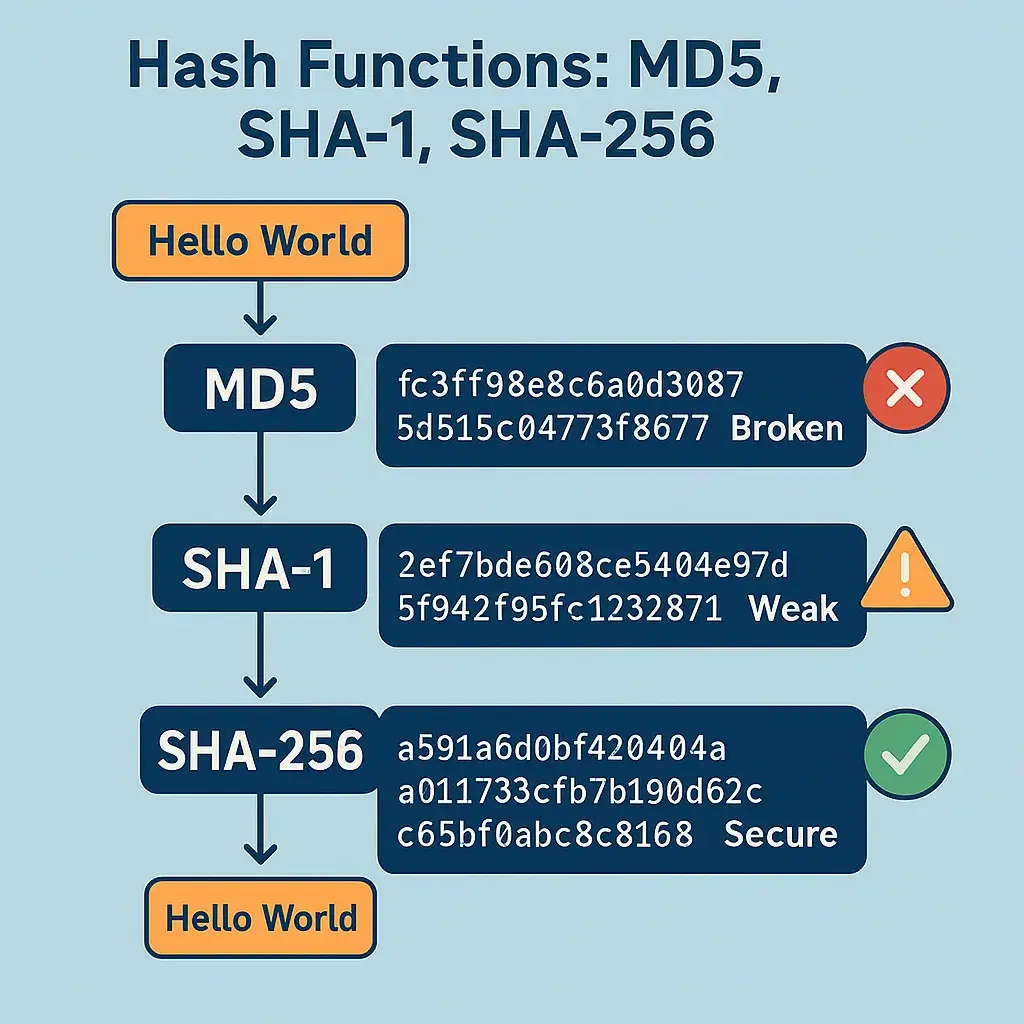
🏛️ Popular Hash Algorithms: MD5, SHA-1, SHA-256
🔸 MD5 (Message Digest 5)
- 📅 Year created: 1992 by Ron Rivest.
- 🔑 Output size: 128-bit (32-character hexadecimal).
Example hash:5d41402abc4b2a76b9719d911017c592 (for input hello)
✔️ Was Used For:
- File integrity checks.
- Password hashing (outdated now).
- Digital signatures (historically).
⚠️ Why It’s Broken:
- ✅ Collision attacks: Hackers can generate two different files with the same hash.
- ✅ Pre-image attacks: Much easier than theoretically expected.
- ✅ Tools can generate fake files with matching MD5 in seconds.
🔥 Today:
- MD5 is considered completely broken for security purposes.
- Only acceptable for quick non-security-related checks like file corruption detection.
🔸 SHA-1 (Secure Hash Algorithm 1)
- 📅 Year created: 1995 by the NSA (National Security Agency).
- 🔑 Output size: 160-bit (40-character hexadecimal).
Example hash:aaf4c61ddcc5e8a2dabede0f3b482cd9aea9434d (for input hello)
✔️ Was Used For:
- SSL/TLS certificates (deprecated).
- Git version control system (slowly migrating away).
- Backup systems, checksums.
⚠️ Why It’s Broken:
- In 2017, Google and CWI Amsterdam performed the first practical collision attack on SHA-1 — known as the SHAttered attack.
- Generating collisions is feasible with today’s computing power.
- SHA-1 is no longer secure for cryptographic purposes.
🔥 Today:
- SHA-1 is deprecated for security-related applications.
- Some legacy systems still use it for non-security checks but should be migrated.
🔸 SHA-256 (Secure Hash Algorithm 256-bit)
- 📅 Year created: 2001 as part of the SHA-2 family.
- 🔑 Output size: 256-bit (64-character hexadecimal).
Example hash:2cf24dba5fb0a30e26e83b2ac5b9e29e1b161e5c1fa7425e73043362938b9824 (for input hello)
✔️ Used For:
- SSL/TLS certificates.
- Bitcoin and most blockchains.
- Password hashing (with salting).
- File verification.
- Digital signatures.
🛡️ Is It Secure?
- As of 2025, SHA-256 is secure.
- No practical collisions or vulnerabilities discovered.
- Recommended for all modern cryptographic tasks.
📎 SHA-3: The Forgotten Hero
🔐 SHA-3 (Keccak) is the latest member of the Secure Hash Algorithm family, standardized by NIST in 2015 as FIPS PUB 202.
✔️ Designed to resist all known attacks and based on sponge construction — unlike the Merkle–Damgård used in SHA-1 and SHA-2.
📦 Use Cases:
- Quantum-resistant cryptography research
- IoT security
- Future blockchain designs
⚠️ Not widely adopted yet, but recommended for systems needing maximum future-proofing or quantum resilience.
⚔️ How Hackers Break Hash Functions
🔁 Hash Attack Flow
[User Input]
↓
[Hash Function]
↓
[Hash Output]
↓
[Attacker Actions]
├── Brute Force (Try every password)
├── Dictionary Attack (Precomputed common hashes)
├── Rainbow Table (Lookup unsalted hash)
├── Collision Attack (Same hash, different input)
└── Birthday Attack (Probability-based collision)
🔥 1. Brute-Force Attack
- Try every possible input until the correct hash is found.
- Effective if passwords are short or simple.
🔥 2. Dictionary Attack
- Use lists of common passwords (like
123456,password,qwerty). - Hashes of these passwords are precomputed and compared.
🔥 3. Rainbow Tables
- Precomputed databases of hashes for all common passwords.
- Extremely effective against unsalted hashes (like MD5 and SHA-1 without salt).
🔥 4. Collision Attack
- Find two different inputs that produce the same hash.
- Effective against MD5 and SHA-1.
🔥 5. Birthday Attack (Mathematical)
- Exploits the birthday paradox to increase the chance of finding a collision.
- Reduces the expected difficulty from
2^nto2^(n/2).
🕵️♂️ Man-in-the-Middle (MITM) Warning
⚠️ MITM Risk:
If you transmit passwords or sensitive data over HTTP instead of HTTPS, attackers can intercept and modify traffic. This is called a Man-in-the-Middle (MITM) attack.🔓 Example:
A login form sends a password overhttp://example.com/login. On a public Wi-Fi, an attacker captures the password in plaintext.✅ Always enforce HTTPS with valid TLS certificates to encrypt all communications.
🛑 How to Protect Against Hash Attacks:
- 🔑 Always use salting. A unique random string added to each password before hashing.
- 🔐 Use slow, resistant hashing algorithms for passwords:
- bcrypt, scrypt, Argon2 (designed to be computationally expensive).
- 🚫 Never use MD5 or SHA-1 for security.
- ✅ Stick to SHA-256, SHA-512, or better for cryptography.
- 🛡️ For passwords, SHA-256 alone is not enough — must combine with salting and stretching (bcrypt, scrypt, Argon2).
- 🔍 Use HMAC (Hash-based Message Authentication Code) for secure authentication processes.
📊 Comparison Tables:
| Algorithm | Year | Output | Status | Security |
|---|---|---|---|---|
| MD5 | 1992 | 128-bit | ❌ Broken | Collision attacks trivial |
| SHA-1 | 1995 | 160-bit | ❌ Broken | Collision practical (Google, 2017) |
| SHA-256 | 2001 | 256-bit | ✅ Secure | No practical attacks |
📊 Password Hashing Algorithms Compared
| Feature | bcrypt | scrypt | Argon2 |
|---|---|---|---|
| Year Introduced | 1999 | 2009 | 2015 (Password Hashing Comp.) |
| Memory Hardness | ❌ Low | ✅ Medium | ✅✅ High (especially Argon2id) |
| CPU Cost | Medium | High | Adjustable |
| Resistance to GPU Attacks | Medium | ✅ Good | ✅✅ Excellent |
| Salting Support | ✅ Yes | ✅ Yes | ✅ Yes |
| Used In | Web apps, CMS | Linux, secure storage | Cryptography, security products |
| Recommended | ✅ Still good | ✅ Strong | ✅✅ Best option (OWASP) |
🔐 Recommendation: Use Argon2id for new systems. If not available, bcrypt with salt remains acceptable. Avoid unsalted MD5/SHA-1 under any circumstances.
✅ Best Practices Checklist for Hashing:
- 🚫 Never use MD5 or SHA-1 for security.
- 🔒 Always use salted hashes for passwords.
- 🛡️ Use bcrypt, scrypt, or Argon2 for password storage.
- 🔐 Use SHA-256, SHA-512 for checksums, blockchain, certificates.
- 🔍 Regularly audit your systems for outdated algorithms.
- 📜 Follow recommendations from NIST (Special Publication 800-107) and OWASP.
📚 Author’s Glossary:
- Hash Function: A one-way function that converts data into a fixed-size string.
- Digest: The output of a hash function (also called hash value).
- Collision: When two different inputs produce the same hash output.
- Pre-image Attack: Trying to recover the original input from a hash.
- Salting: Adding random data to input before hashing to prevent rainbow table attacks.
- Rainbow Table: A precomputed database of hashes for reversing weak hashes.
- Brute-Force: Trying every possible combination to find a hash match.
- HMAC: A keyed hash used for message authentication.
- SHA (Secure Hash Algorithm): A family of cryptographic hash functions developed by the NSA.
- bcrypt / scrypt / Argon2: Modern password hashing algorithms designed to resist brute-force attacks.
🏁 Conclusion:
Hash functions are a critical part of cybersecurity — from verifying data integrity to storing passwords securely. However, not all hash functions are equal. MD5 and SHA-1 are broken and dangerous for security. SHA-256 remains secure and reliable as of today.
Understanding how hashes work — and how attackers try to break them — is essential for anyone working in cybersecurity, IT, or even as an everyday user who values privacy and data protection.