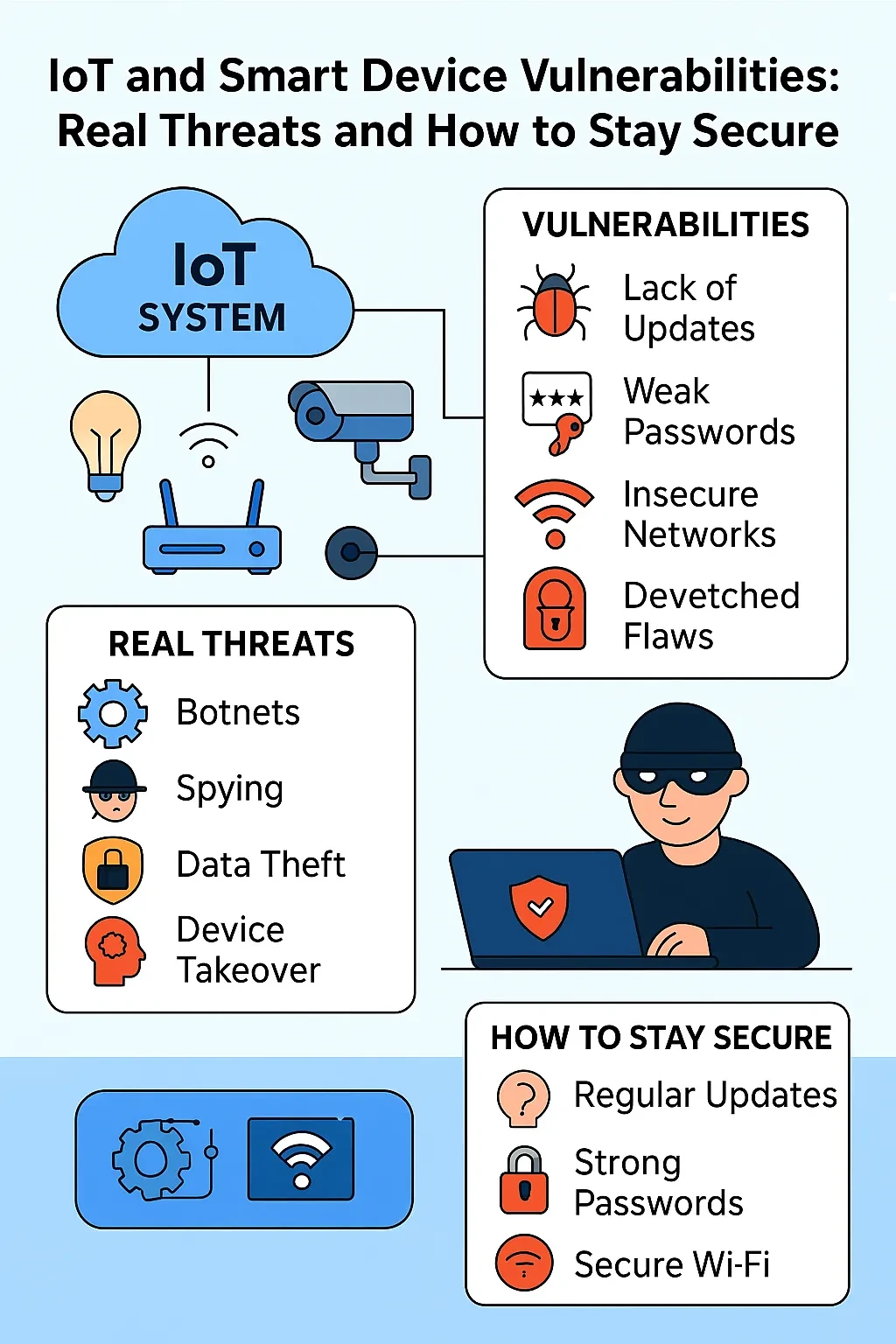
🧠 Introduction The Internet of Things (IoT) is revolutionizing how we live — from smart thermostats and connected doorbells to industrial sensors and medical implants. However, this connectivity also introduces new security challenges. Many IoT devices lack robust security features, making them attractive targets for cybercriminals.
⚠️ Disclaimer This article is written for educational and ethical purposes only. It aims to help readers understand real security threats related to IoT and smart devices, and how to defend against them.
In this article, we explore:
- What makes IoT devices vulnerable
- Real-world attacks on smart devices
- Practical steps to protect yourself and your network
- Tools, best practices, and expert recommendations
📦 What Are IoT and Smart Devices? IoT devices are physical objects equipped with sensors, software, and network connectivity that allow them to collect and exchange data over the internet. These devices function autonomously or semi-autonomously and are often designed for specific purposes.
🔌 Examples:
- Consumer: Smart TVs, smart locks, fitness trackers, voice assistants (e.g., Alexa)
- Industrial: SCADA systems, factory sensors, energy grid monitors
- Medical: Pacemakers, insulin pumps, wearable health monitors
These devices gather vast amounts of sensitive data and are frequently overlooked in cybersecurity planning, especially in home and small business environments.
🚨 Why IoT Devices Are Vulnerable
| Reason | Description |
|---|---|
| Weak default credentials | Many devices use common logins like “admin/admin” or “1234” that remain unchanged |
| Lack of updates | Firmware updates are infrequent, leaving known vulnerabilities exposed |
| Insecure communication | Many devices communicate over HTTP instead of HTTPS, or expose open ports |
| Limited processing power | Many lack resources to support antivirus or encryption |
| Vendor neglect | Manufacturers often prioritize cost and convenience over security |
| Complex supply chains | Third-party components may introduce hidden vulnerabilities |
| No standardization | Security practices vary widely across vendors |
🛑 Real-World IoT Attacks
- Mirai Botnet (2016)
Over 600,000 IoT devices were infected and turned into a botnet for launching massive DDoS attacks on sites like Twitter and Netflix. Attackers exploited default credentials. - Ring Doorbell Hacks (2019)
Hackers accessed home Ring cameras using reused passwords and lack of 2FA. In one case, a hacker spoke to a child through the device. - St. Jude Medical Devices (2017)
Researchers found that St. Jude pacemakers were vulnerable to remote exploitation. The U.S. FDA later confirmed the risk and issued guidance. - Jeep Cherokee Hack (2015)
Researchers took remote control of a Jeep’s steering and brakes via its infotainment system. Over 1.4 million vehicles were recalled. - Water Utility Hack in Florida (2021)
A hacker remotely accessed a water treatment facility’s system and attempted to increase the amount of sodium hydroxide in the water. Fortunately, an operator noticed the intrusion and prevented harm. - Smart Lightbulbs and Voice Assistants Exploits
Researchers have demonstrated attacks where vulnerabilities in smart bulbs or voice assistants could expose Wi-Fi credentials or be used as an entry point to wider networks.
🧱 How an IoT Attack Chain Works (ASCII Diagram)
scss[Internet] → [Router] → [IoT Device]
↑
(Botnet / Exploit)
Attackers can hijack vulnerable devices by scanning for open ports, default credentials, or outdated firmware — then turn them into part of a botnet or use them as a pivot point into the wider network.
🧰 How IoT Attacks Work Default Credential Exploit
Once inside, an attacker can:
- Install malware
- Hijack the device for spying
- Add the device to a botnet
Unencrypted Data Sniffing Using a packet sniffer like Wireshark, attackers can intercept login data from unencrypted devices:
Remote Exploitation via Vulnerable Firmware Outdated firmware may have unpatched vulnerabilities. An attacker can scan for exposed ports or services, then upload malicious code.
Man-in-the-Middle (MITM) Attacks If traffic is unencrypted, attackers can intercept and alter communication between the IoT device and the cloud.
🚨 High-Risk Smart Devices
| Device Type | Risk Level | Why It’s Risky |
|---|---|---|
| Smart Cameras | 🔴 High | Always on, often cloud-connected, prone to spying |
| Smart TVs | 🟠 Medium | Third-party apps and outdated firmware |
| Wi-Fi Printers | 🔴 High | Frequently expose open ports, rarely updated |
| Medical Implants | 🔺 Critical | Exploits can threaten patient safety |
Pro Tip: Many of these devices ship with weak credentials and no automatic patching. Treat each one like a tiny computer — and secure it accordingly.
✅ Essential Protection Checklist
| Task | Description |
| 🔑 Change default passwords | Use unique, strong passwords for every device |
| 🔄 Keep firmware updated | Regularly check and apply vendor security updates |
| 🔒 Use network segmentation | Place IoT on a separate VLAN or guest network |
| 🔐 Enable HTTPS or VPNs | Ensure secure data transmission channels |
| 📱 Enable 2FA | Add extra login protection where available |
| 📵 Disable unused services | Turn off features like remote access if not needed |
| 🌐 Disable UPnP | Prevent devices from opening ports without notice |
| 🔍 Monitor network traffic | Use tools like Wireshark or Fing to spot anomalies |
| 🚫 Limit external access | Only allow remote access via secured channels |
🧠 Advanced Strategies for Organizations
- Network Behavior Monitoring: Use IDS/IPS tools to spot abnormal activity.
- Zero Trust Architecture: Require authentication for every device.
- Device Inventory & Risk Scoring: Track all IoT devices and assess their risks.
- IoT Gateways: Use gateways to control, monitor, and encrypt device traffic.
- Vendor Vetting: Only use devices from companies with strong security policies.
- Access Control Lists (ACLs): Limit what IoT devices can communicate with.
- Security by Design: Include IoT security in procurement and development processes.
❓ FAQ (Frequently Asked Questions)
Q1: Should I disconnect IoT devices when not in use?
Yes. If a device isn’t essential 24/7, disconnecting it reduces the risk.
Q2: Can IoT devices be hacked without internet access?
Yes — if they’re on a local network with open ports or weak credentials.
Q3: How do I know if a device has been compromised?
Look for slowdowns, odd behavior, unexpected reboots, or strange network traffic.
Q4: Is it safe to use smart home gadgets at all?
Yes — if you follow security best practices: strong passwords, updates, and 2FA.
Q5: How can I isolate IoT from other devices?
Set up a guest or VLAN network for your smart gadgets using your router settings.
Q6: What tools can help secure my IoT devices?
Tools like Fing, Nmap, Wireshark, and firewalls can help monitor and protect your network.
Q7: What’s the role of AI in IoT security?
AI is increasingly used in threat detection, anomaly monitoring, and automated response systems.
📚 Sources
- KrebsOnSecurity: Mirai Botnet Origin Story
- Wired: Hackers Remotely Kill a Jeep on the Highway
- FDA.gov: Cybersecurity Vulnerabilities in Medical Devices
- Ring Security Reports (2019)
- SC Magazine, 2024 IoT Security Roundup
- ENISA Guidelines for IoT Security (2025)
📖 Glossary
| Term | Definition |
| IoT | Internet of Things: networked smart devices |
| Botnet | A group of hijacked devices used for cyberattacks |
| 2FA | Two-Factor Authentication: adds another step to the login process |
| Firmware | The software permanently programmed into a device |
| IDS/IPS | Intrusion Detection/Prevention Systems: tools for detecting cyber threats |
| Zero Trust | A security model where no device or user is trusted by default |
| MITM | Man-in-the-Middle: attacker intercepts communication between two parties |
| VLAN | Virtual LAN: a separate logical network for isolating traffic |
| ACL | Access Control List: defines rules to limit device communication |