🏛️ What Is OWASP and the Top 10?
The OWASP (Open Worldwide Application Security Project) is a global nonprofit organization focused on improving software security. One of their most famous projects is the OWASP Top 10, which lists the ten most critical web application security risks.
✔️ This list is widely recognized as an industry standard for understanding and mitigating web vulnerabilities.
⚠️ Disclaimer
This article is written for educational and ethical purposes only. Its purpose is to help readers understand the most common web vulnerabilities listed in the OWASP Top 10, how attackers exploit them, and how to protect against them. The information provided is not intended for illegal use.
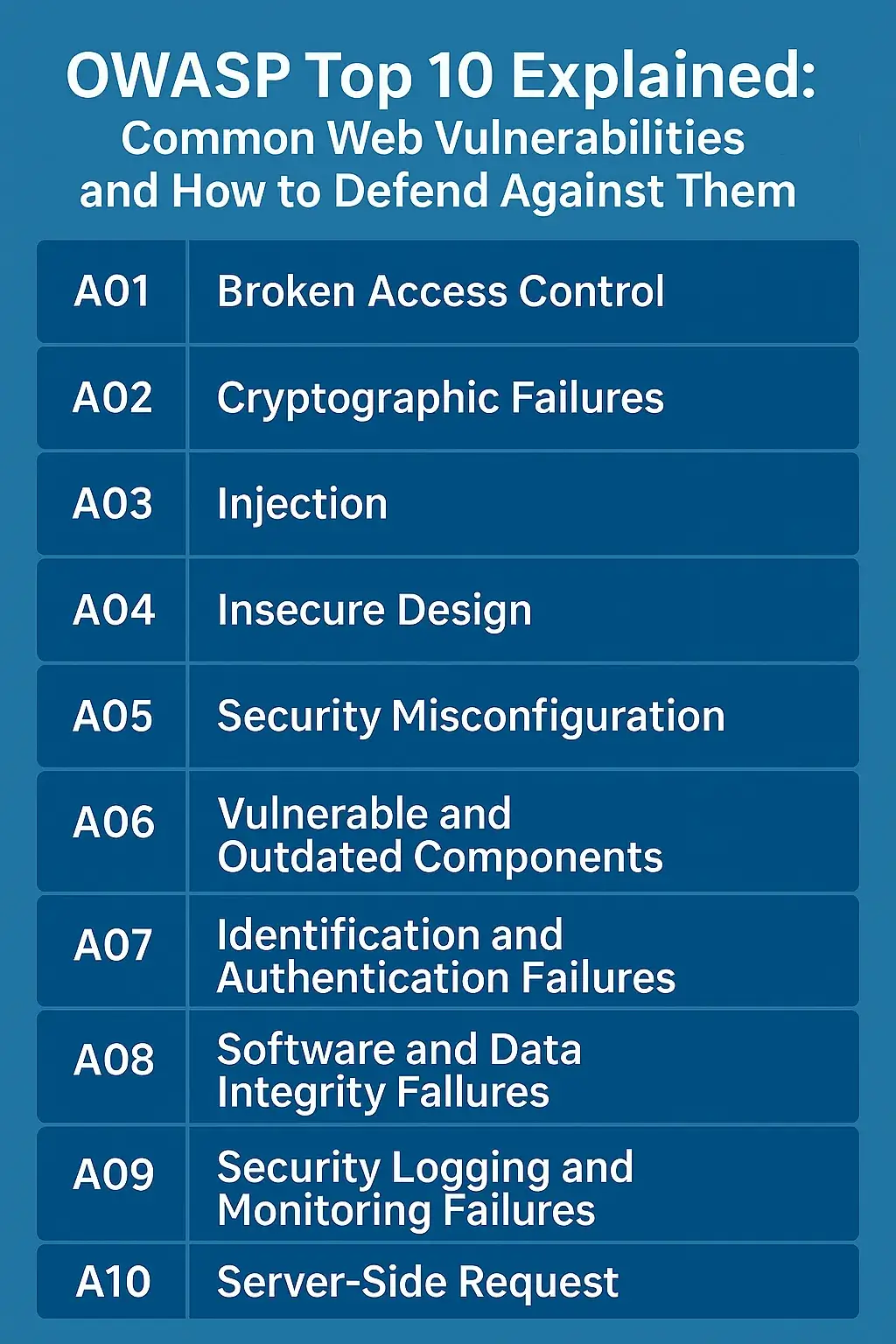
🚩 OWASP Top 10 — Full Breakdown (2021/2023 Update)
1. Broken Access Control (A01)
🔥 What It Is:
When users can access data, functions, or resources they shouldn’t. This occurs when access controls are misconfigured or missing.
⚠️ Examples:
- Viewing another user’s account by changing the URL (
/account/123to/account/124). - Accessing admin panels without authorization.
🛠️ How Attackers Exploit:
- Direct object reference manipulation.
- Forced browsing to restricted URLs.
🏰 Defense:
- Enforce server-side authorization checks.
- Deny by default — allow only what’s needed.
- Use proper role-based access controls.
2. Cryptographic Failures (A02)
🔥 What It Is:
Previously called “Sensitive Data Exposure”, this occurs when sensitive data (passwords, credit cards) isn’t properly protected.
⚠️ Examples:
- Using outdated encryption like MD5 or SHA-1.
- Sending passwords or payment data over HTTP instead of HTTPS.
🛠️ How Attackers Exploit:
- Sniffing data over insecure networks.
- Stealing poorly stored credentials.
🏰 Defense:
- Use HTTPS/TLS everywhere.
- Encrypt data at rest and in transit with strong algorithms (AES, SHA-256, RSA).
- Never store plaintext passwords — use salted hashes with bcrypt or Argon2.
3. Injection (A03)
🔥 What It Is:
Occurs when untrusted input is sent to an interpreter (SQL, NoSQL, OS commands), tricking the application into executing malicious commands.
⚠️ Examples:
- SQL Injection:
' OR '1'='1 - OS Injection:
; rm -rf /this is a simplified example
🛠️ How Attackers Exploit:
- Input fields not sanitized.
- Manipulating API parameters.
🏰 Defense:
- Use parameterized queries (prepared statements).
- Employ input validation and output encoding.
- Apply least privilege to databases.
4. Insecure Design (A04)
🔥 What It Is:
Fundamental flaws in the design phase that lead to security gaps. This is about bad architecture, not coding mistakes.
⚠️ Examples:
- No authentication for sensitive operations.
- Not considering abuse scenarios.
🛠️ How Attackers Exploit:
- Exploit missing security controls.
- Abuse poorly designed APIs.
🏰 Defense:
- Apply threat modeling during design.
- Use secure development lifecycle (SDLC).
- Implement security by design principles.
5. Security Misconfiguration (A05)
🔥 What It Is:
When security settings are incorrect or left at default.
⚠️ Examples:
- Default admin credentials left unchanged.
- Directory listing enabled.
- Unnecessary features enabled (debug mode, verbose errors).
🛠️ How Attackers Exploit:
- Scan for open admin panels or sensitive files.
- Exploit exposed services and debug endpoints.
🏰 Defense:
- Harden all environments (dev, staging, production).
- Disable unnecessary services.
- Automate security configuration checks.
6. Vulnerable and Outdated Components (A06)
🔥 What It Is:
Using libraries, frameworks, or software with known vulnerabilities.
⚠️ Examples:
- Running an outdated WordPress plugin with security flaws.
- Using a vulnerable JavaScript library like jQuery.
🛠️ How Attackers Exploit:
- Find known CVEs (Common Vulnerabilities and Exposures).
- Exploit unpatched systems or libraries.
🏰 Defense:
- Keep dependencies up to date.
- Use software composition analysis (SCA) tools (e.g., Snyk, Dependabot).
- Remove unused libraries.
7. Identification and Authentication Failures (A07)
🔥 What It Is:
Weak or broken authentication mechanisms.
⚠️ Examples:
- Brute-force login allowed.
- No multi-factor authentication (MFA).
- Weak password requirements.
🛠️ How Attackers Exploit:
- Credential stuffing with leaked passwords.
- Brute-force attacks.
🏰 Defense:
- Enforce strong password policies.
- Implement MFA.
- Lock accounts after repeated failed attempts.
8. Software and Data Integrity Failures (A08)
🔥 What It Is:
Occurs when software updates, CI/CD pipelines, or data are not verified for integrity.
⚠️ Examples:
- Failing to verify code dependencies from external sources.
- Insecure software updates without signature validation.
🛠️ How Attackers Exploit:
- Supply chain attacks (e.g., SolarWinds breach).
- Inject malicious code into update processes.
🏰 Defense:
- Use digital signatures for code and updates.
- Implement secure CI/CD pipelines with integrity checks.
9. Security Logging and Monitoring Failures (A09)
🔥 What It Is:
Inadequate logging, monitoring, and alerting. Allows attackers to operate undetected.
⚠️ Examples:
- No logs of failed login attempts.
- No alerts for suspicious activity.
🛠️ How Attackers Exploit:
- Perform brute-force, injection, or privilege escalation attacks unnoticed.
🏰 Defense:
- Implement centralized logging.
- Set up real-time alerts for anomalies.
- Regularly review and audit logs.
10. Server-Side Request Forgery (SSRF) (A10)
🔥 What It Is:
Occurs when an attacker tricks the server into sending requests to unintended destinations, often internal systems.
⚠️ Examples:
- Forcing a server to request
http://localhost/adminor cloud metadata endpoints (http://169.254.169.254).
🛠️ How Attackers Exploit:
- Abuse URL fetch features (image previews, webhooks).
- Send requests to internal networks or cloud services.
🏰 Defense:
- Validate and sanitize all URLs.
- Block requests to internal IP ranges.
- Implement network-level protections (firewalls, ACLs).
🏗️ Summary Table — OWASP Top 10
| # | Name | Risk Example | Status |
|---|---|---|---|
| A01 | Broken Access Control | URL manipulation | Critical |
| A02 | Cryptographic Failures | No HTTPS, weak encryption | High |
| A03 | Injection | SQL/OS/NoSQL injection | Critical |
| A04 | Insecure Design | Missing authentication in functions | High |
| A05 | Security Misconfiguration | Default passwords, open directories | High |
| A06 | Vulnerable and Outdated Components | Old libraries, CVEs exploited | High |
| A07 | Identification & Authentication Failures | Weak passwords, no MFA | High |
| A08 | Software & Data Integrity Failures | Supply chain attack | High |
| A09 | Security Logging & Monitoring Failures | No logs/alerts | Medium |
| A10 | Server-Side Request Forgery (SSRF) | Access internal systems via server | High |
✅ Best Practices Checklist:
- 🔒 Implement proper access control — deny by default.
- 🔐 Use strong encryption (AES, SHA-256, TLS).
- 🧹 Sanitize all user inputs (defend against injection).
- 🏗️ Apply secure design principles.
- ⚙️ Harden server configurations.
- 🧰 Regularly update dependencies — patch CVEs.
- 🔑 Enforce MFA and strong authentication policies.
- 🏗️ Secure software supply chains with integrity checks.
- 📜 Enable centralized logging and real-time alerts.
- 🔍 Sanitize all external requests to prevent SSRF.
📚 Author’s Glossary:
- OWASP: Open Worldwide Application Security Project — nonprofit focused on web security.
- SQL Injection: Inserting malicious SQL commands into queries.
- SSRF (Server-Side Request Forgery): Forcing a server to make internal network requests.
- XSS (Cross-Site Scripting): Injecting malicious scripts into websites (formerly in OWASP Top 10).
- CVE: Common Vulnerabilities and Exposures — catalog of known software vulnerabilities.
- Supply Chain Attack: Compromising third-party software or updates to infect downstream systems.
- Brute-force Attack: Attempting many password combinations until successful.
- CI/CD: Continuous Integration/Continuous Deployment — pipelines for automatic code delivery.
- ACL (Access Control List): Network security mechanism to allow/deny traffic.
🏁 Conclusion:
The OWASP Top 10 is not just a list — it’s a blueprint of the most common and dangerous mistakes in web application security. Whether you are a developer, system administrator, or cybersecurity professional, understanding and mitigating these vulnerabilities is essential for building safe applications and protecting users.