🧠 Understanding Ports Is Critical for Cybersecurity.
⚠️ Disclaimer
This article is written for educational and ethical purposes only. Its goal is to help readers understand how TCP/UDP ports and protocols work, how they are used in both cyberattacks and cybersecurity defense.
🚩 What Are Ports in Networking?
A port is a virtual door on a device that allows specific types of network traffic in or out.
✔️ IP address = building address.
✔️ Port = specific room or office inside the building.
→ Example:
- IP:
192.168.1.10 - Port
443= HTTPS (secure web traffic)
🔥 TCP vs UDP — The Two Main Transport Protocols
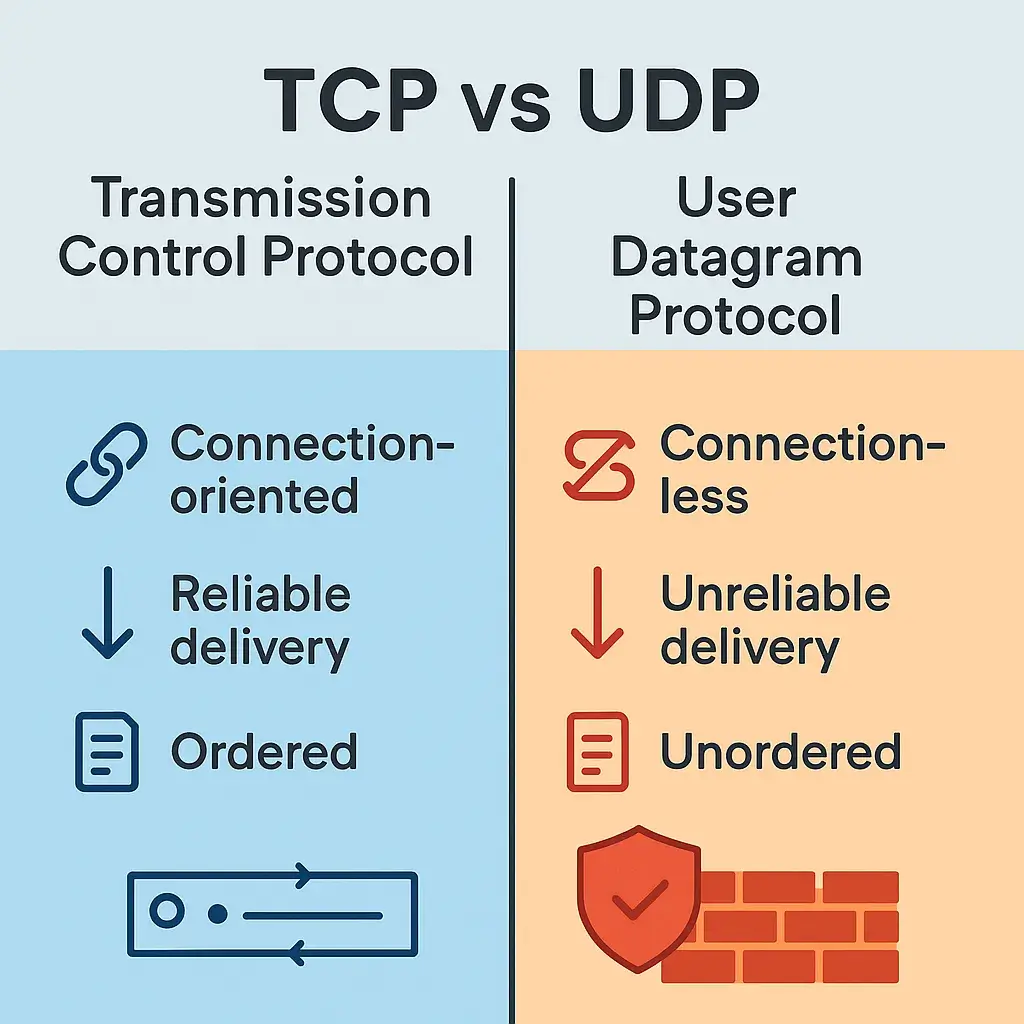
✅ TCP (Transmission Control Protocol)
✔️ Reliable, connection-based protocol.
✔️ Uses 3-way handshake: SYN → SYN-ACK → ACK.
✔️ Guarantees delivery, order, and error checking.
Used for:
- Websites (HTTPS/HTTP)
- Email (SMTP/IMAP/POP3)
- File transfers (FTP, SFTP)
- Remote access (SSH)
🔄 ASCII Diagram: TCP 3-Way Handshake
Place this in the section explaining how TCP works:
plaintext🔄 TCP 3-Way Handshake:
Client Server
| SYN (Hello) |
|---------------------------> |
| |
| SYN-ACK (Hello back) |
| <-------------------------- |
| |
| ACK (Let's talk) |
|---------------------------> |
| |
🔐 Secure, reliable connection established
This clearly illustrates how TCP establishes a reliable connection — especially helpful for beginners.
✅ UDP (User Datagram Protocol)
✔️ Connectionless, faster but unreliable.
✔️ No handshake, no guarantees.
Used for:
- Streaming (YouTube, Netflix)
- Gaming (Fortnite, CS:GO)
- Voice/video calls (Zoom, WhatsApp)
- DNS (Domain Name System) queries
🏴☠️ How Hackers Use Ports and Protocols
🔥 1. Port Scanning (Reconnaissance)
✔️ Hackers scan for open ports using special tools .
✔️ Open ports reveal services running on the target:
→ Port 22 — SSH (remote access)
→ Port 445 — SMB (file sharing — infamous for WannaCry)
→ Port 3389 — RDP (Remote Desktop Protocol)
🔥 2. Exploiting Vulnerable Services
✔️ If outdated or misconfigured services are running:
- Port
445: EternalBlue exploit (WannaCry, NotPetya). - Port
80/443: Web application attacks (SQL injection, XSS). - Port
21: FTP brute-force attacks.
🔥 3. UDP-based Attacks
- DNS Amplification (Port 53 UDP): Reflection DDoS.
- NTP Amplification (Port 123 UDP): Abuse for massive DDoS.
- SSDP (Port 1900 UDP): IoT-based reflection attacks.
🔥 4. Backdoors & Malware C2 (Command and Control)
✔️ Malware opens hidden ports to communicate with attackers.
✔️ Common backdoor ports: 4444, 1337, 6666.
✔️ Malware often uses TCP for reliability or UDP for stealth.
🎯 Table: Common Ports and Associated Threats
This maps specific port numbers to well-known attacks:
| Port | Protocol | Common Threats | Exploited By |
|---|---|---|---|
| 21 | FTP | Brute-force, credential theft | Hackers, malware |
| 22 | SSH | Credential stuffing, reverse shells | Pentesters, attackers |
| 53 | DNS | Spoofing, DDoS amplification | Botnets, exploit kits |
| 80 | HTTP | XSS, SQL injection, MITM | Web attackers |
| 123 | NTP | Reflection-based DDoS | IoT botnets |
| 135–139 | NetBIOS | Enumeration, worm propagation | Worms like Conficker |
| 445 | SMB | EternalBlue, ransomware payloads | WannaCry, NotPetya |
| 3389 | RDP | Remote takeover, brute-force | APTs, ransomware groups |
| 4444 | TCP | Metasploit reverse shells | Exploit frameworks |
| 8080 | HTTP-Alt | Proxy abuse, secondary web access |
🔥 5. Reverse Shells
✔️ Attacker forces victim’s machine to connect back to them on a specific port (bypasses firewall outbound rules).
🛡️ How Defenders Use Ports and Protocol Knowledge
🔥 1. Firewall Rules
✔️ Block unused ports.
✔️ Allow only necessary inbound/outbound traffic.
→ Example:
- Allow
443(HTTPS), block21(FTP) if unused.
🧭 Table: Default Open Ports in Windows/Linux
| OS | Default Open Ports | Purpose / Risk |
|---|---|---|
| Windows | 135–139, 445 | NetBIOS/SMB — used by worms and exploits |
| Windows | 3389 | RDP — exposed to credential attacks |
| Linux | 22 | SSH — brute-force or key guessing |
| Linux | 631 | CUPS — exposed printer interface |
| Both | 5353 | mDNS — service discovery leaks |
| IoT | 23, 2323 | Telnet — legacy protocol, weak auth |
🔍 Tip: Use netstat -tulnp to audit these regularly.
🔥 2. Intrusion Detection Systems (IDS)
✔️ Tools like Snort, Suricata monitor port-based traffic patterns.
✔️ Alert on suspicious activities (e.g., port scanning, malformed TCP flags).
🔥 3. Port Knocking
✔️ A stealth security technique — only opens a port after a correct sequence of connection attempts.
→ Example: Knock on 5000, then 6000, then 7000 → Opens SSH on 22.
🔥 4. Honeypots on Common Ports
✔️ Deploy fake services on juicy ports (22, 445, 3389) to detect attackers.
✔️ Example tools: Cowrie (SSH honeypot).
🔥 5. Network Segmentation
✔️ Restrict services to specific network segments.
✔️ Example: Database server listening on 3306 (MySQL) is only accessible internally, not from the internet.
🧠 Common TCP/UDP Ports Cheat Sheet
| Port | Protocol | Service | Common Use |
|---|---|---|---|
| 21 | TCP | FTP | File Transfer |
| 22 | TCP | SSH | Secure Remote Access |
| 25 | TCP | SMTP | Email Sending |
| 53 | UDP/TCP | DNS | Domain Name Resolution |
| 80 | TCP | HTTP | Web Traffic |
| 110 | TCP | POP3 | Email Retrieval |
| 123 | UDP | NTP | Network Time Protocol |
| 143 | TCP | IMAP | Email Retrieval |
| 161 | UDP | SNMP | Network Management |
| 443 | TCP | HTTPS | Secure Web Traffic |
| 445 | TCP | SMB | File Sharing (Windows) |
| 3306 | TCP | MySQL | Database |
| 3389 | TCP | RDP | Remote Desktop |
| 5060 | UDP/TCP | SIP | VoIP Communication |
| 8080 | TCP | HTTP (Alternate) | Web Proxy / Web Apps |
🚫 Common Mistakes
- ❌ Leaving unnecessary ports open.
- ❌ Assuming UDP is safe because it’s connectionless.
- ❌ Misconfiguring firewalls (e.g., open
3389to the world). - ❌ Ignoring outbound connections (malware loves this).
- ❌ Relying solely on security through obscurity (e.g., changing SSH from
22to2222— not enough).
🚀 Checklist for Port Security
- 🔲 Scan your own network regularly (Nmap).
- 🔲 Disable unused services and ports.
- 🔲 Harden necessary services (e.g., SSH with keys).
- 🔲 Deploy IDS/IPS to monitor traffic.
- 🔲 Use firewalls aggressively (block all → allow only necessary).
- 🔲 Monitor outbound connections for malware C2.
🏆 Final Thoughts
Ports are the front doors of your network. Hackers jiggle the handles — defenders lock the right ones.
✔️ Mastering TCP/UDP and port behavior is cybersecurity 101.
→ If you don’t understand your open ports, attackers will.
✅ Sources Used
- Cybersecurity and Infrastructure Security Agency (CISA)
- OWASP Port Security Guidelines
- NIST TCP/UDP Network Security Standards
- FBI IC3 Report 2023
- SANS Institute TCP/UDP Threat Reports
📖 Glossary — Key Terms
- Port: Logical communication endpoint for a device.
- TCP: Reliable connection-oriented protocol.
- UDP: Fast, connectionless protocol.
- Nmap: Network scanning tool.
- Firewall: Security device that controls network traffic.
- IDS/IPS: Intrusion Detection/Prevention System.
- Reverse Shell: Attack technique where a victim connects back to an attacker.
- Port Knocking: Stealth access technique based on port sequences.