⚠️ Disclaimer
This article is strictly educational and complies with all applicable laws. It does not promote or endorse any illegal activity. Always use technology responsibly.
🧠 Introduction: That Tiny Chip Controls Your Digital Life
You probably don’t think about it, but the SIM card inside your phone is the key to your identity in the mobile world.
It’s smaller than your fingernail, easy to overlook, and yet it connects you to banks, emails, social networks, and even medical records. It’s not just a chip — it’s your digital passport, and like any passport, it can be stolen, cloned, or faked.
So what exactly is a SIM card? How does it work? And why have hackers, scammers, and surveillance agencies become so obsessed with it?
Let’s break it all down — from history and types to threats and defense.
📜 A Brief History of SIM Cards
| Year | Milestone |
|---|---|
| 1991 | GSM standard introduced by ETSI — the birth of the SIM concept |
| 1992 | First commercial SIM cards released in Europe |
| Early 2000s | Widespread global adoption with GSM/3G networks |
| 2012 | Introduction of nano-SIM format |
| 2016 | Rise of eSIM (embedded SIM) |
| 2023+ | Start of iSIM (integrated SIM into the processor) |
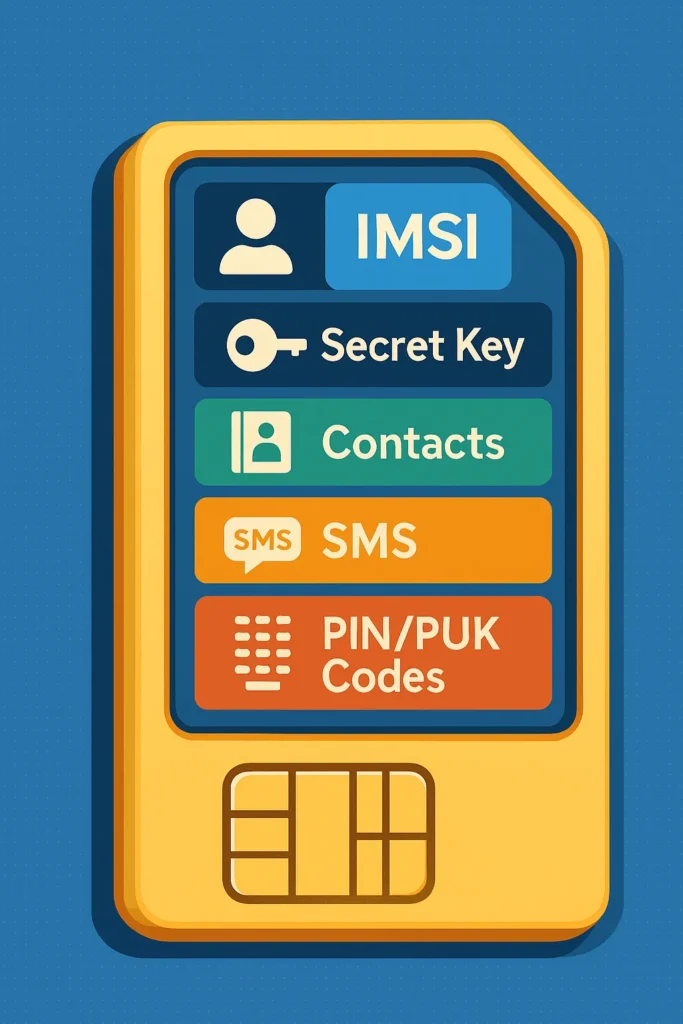
SIM stands for Subscriber Identity Module — a small, removable smart card that stores your IMSI (International Mobile Subscriber Identity), encryption keys, and authentication data.
Initially, SIMs were the size of credit cards. Today, they’ve shrunk to embedded microchips — but their role has grown immensely.
🔍 What Exactly Is a SIM Card?
A SIM card is a secure element that performs these core functions:
- Identifies you to the mobile network
- Stores your phone number and IMSI
- Handles authentication and encryption
- Provides access to SMS, data, and voice services
- Sometimes stores contacts or small apps (like mobile banking)
It’s your personal license to connect to a mobile carrier.
🔄 Types of SIM Cards
| Type | Description |
|---|---|
| Full-size SIM | Obsolete; size of a credit card |
| Mini-SIM | Standard SIM, used in early phones (25×15 mm) |
| Micro-SIM | Smaller format (15×12 mm), used in older smartphones |
| Nano-SIM | Modern format (12.3×8.8 mm), used today |
| eSIM | Embedded into the phone’s hardware — not removable |
| iSIM | Integrated directly into the CPU or modem; future standard |
🛠️ How SIM Authentication Works
- Phone sends IMSI (a unique number stored in the SIM) to the network.
- Network responds with a random number.
- SIM uses its secret Ki key to compute a response.
- If the result matches what the network expects — you’re authenticated.
⚠️ If someone steals your SIM — they impersonate you.
💣 SIM-Related Cyber Threats
1. SIM Swapping (SIM-Swap Fraud)
A hacker tricks your carrier into porting your number to their SIM — and hijacks 2FA, banking, crypto.
Real Case:
In 2019, a teen in the U.S. stole $24 million in crypto using SIM swaps.
2. SIM Cloning
An attacker duplicates the SIM and intercepts your messages and calls. Rare but possible with physical access and old SIMs.
3. SS7 Exploits
SS7 is the protocol that mobile networks use to talk to each other. It’s notoriously insecure — allowing location tracking, call interception, and more.
4. Baseband Attacks / IMSI Catchers
Devices like Stingrays simulate cell towers and trick your phone into connecting. Then, they can read your IMSI, metadata, and in some cases, data.
🧬 The Evolution: From SIM to eSIM and iSIM
| SIM Type | Physical? | Reprogrammable? | Security Risk |
|---|---|---|---|
| SIM | Yes | No | Medium |
| eSIM | No (embedded) | Yes | High if misconfigured |
| iSIM | No (CPU-level) | Yes | TBD |
- eSIM makes remote provisioning possible — one QR code can activate your number.
- iSIM is the future of machine-to-machine authentication (IoT, smart cars, AI drones).
But with power comes new risks — remote takeover, provisioning attacks, and loss of user control.
🧰 How to Protect Yourself
| Threat | Protection |
|---|---|
| SIM Swap | Use carrier PIN, freeze number changes |
| Cloning | Don’t share your SIM; upgrade to newer SIM |
| SS7 Attacks | Use encrypted apps (Signal, WhatsApp) |
| eSIM Hijack | Don’t scan QR codes from untrusted sources |
| IMSI Catchers | Use airplane mode in high-risk areas |
Bonus Tips:
- Never post your phone number online.
- Separate your number from your most sensitive accounts.
- Use app-based 2FA (TOTP) instead of SMS.
🧠 GLOSSARY
- SIM – Subscriber Identity Module
- IMSI – International Mobile Subscriber Identity
- Ki – Secret authentication key stored on the SIM
- eSIM – Embedded SIM, programmable chip soldered into device
- iSIM – Integrated SIM, built directly into processor
- SS7 – Signaling System No. 7, a telecom protocol used worldwide
- IMSI Catcher – A fake cell tower used for surveillance
- SIM Swap – Fraudulent porting of your number to another SIM
❓ FAQ
Q: Can a SIM card be hacked remotely?
A: Not directly — but if your carrier is compromised or social-engineered, yes.
Q: Is eSIM safer than traditional SIM?
A: Not necessarily — it has different risks, especially during provisioning.
Q: Should I disable SMS-based 2FA?
A: Yes. Use app-based authentication (e.g., Google Authenticator or Authy).
Q: Can someone track my location through my SIM?
A: Yes, via network triangulation or SS7 vulnerabilities.
Q: What happens if I lose my SIM card?
A: Call your carrier immediately to suspend or replace it.
🔚 Conclusion: The Smallest Chip with the Biggest Responsibility
In a world that’s increasingly mobile-first, your SIM card isn’t just a tool — it’s your authentication token, identity beacon, and security weak point all in one.
As eSIMs and iSIMs take over, we gain flexibility — but also open the door to new attacks. Understanding how this small chip works is no longer optional — it’s foundational digital literacy.
Treat your SIM like you treat your passport or your keys. Because in the wrong hands, it’s far more dangerous than you think.