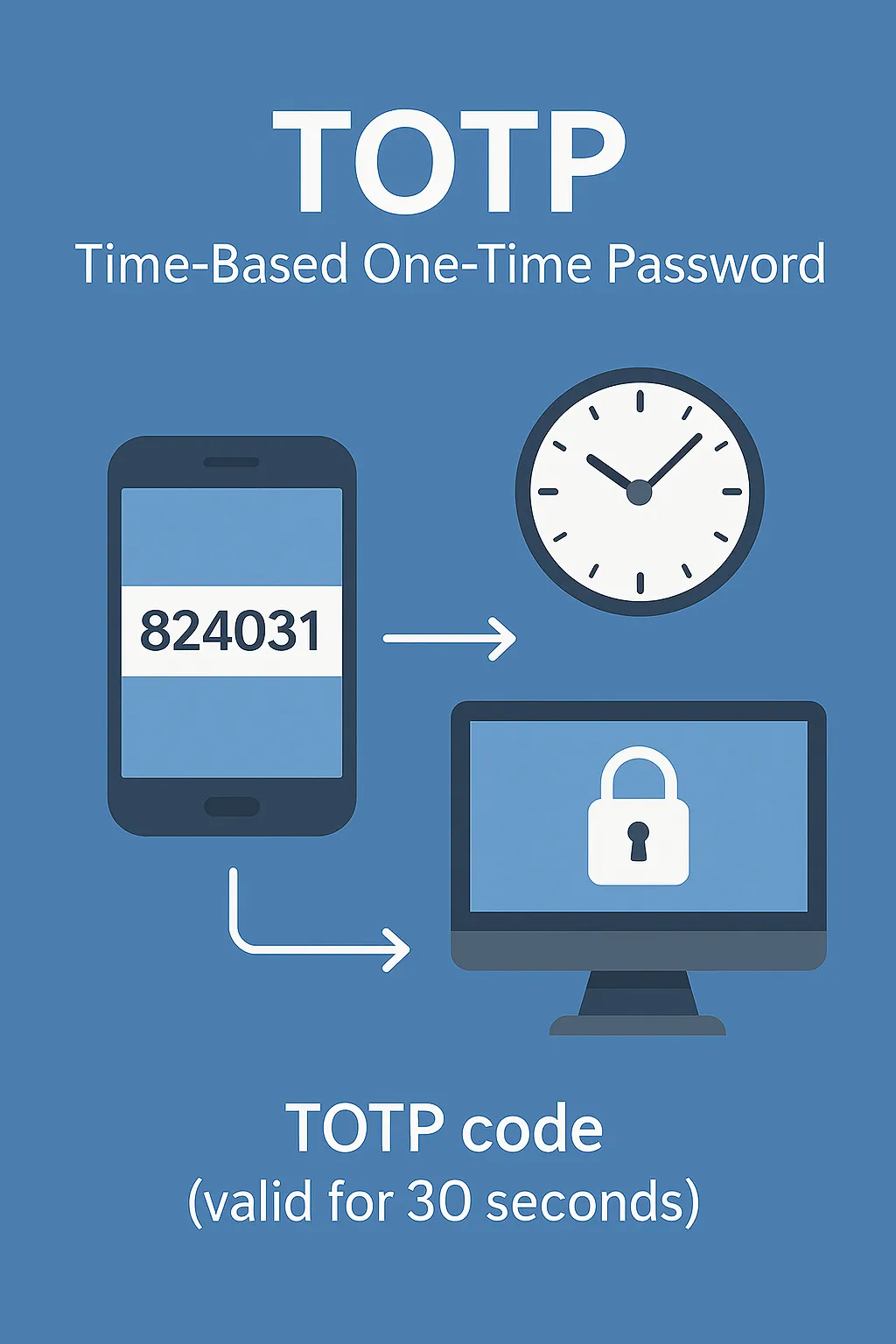
TOTP (Time-Based One-Time Password) is a temporary, numeric code used as a second layer of security in two-factor authentication (2FA). The code is generated locally on your device and changes every 30 seconds based on the current time and a shared secret key. TOTP is widely used in banking, cloud services, and developer platforms.
📘 Definition
TOTP is a time-based algorithm that produces one-time codes. It’s based on a cryptographic method called HMAC (Hash-based Message Authentication Code) and uses the current time as a changing factor. Both the server and the user’s device calculate the code independently but synchronously, without needing to exchange the code in advance.
This makes it more secure than SMS-based 2FA, which is vulnerable to SIM swapping, interception, and delays.
🧪 Technical Details
TOTP is defined in the official internet standard RFC 6238, and builds on the HOTP (HMAC-based One-Time Password) method, replacing HOTP’s counter-based system with time intervals.
🔣 Algorithm Formula
TOTP = Truncate(HMAC-SHA1(secret, T))
secret– A unique cryptographic key shared between the server and the user’s device. This key is usually embedded in a QR code during TOTP setup and must be kept secret.T– A time-based counter representing the number of 30-second periods since Unix epoch (January 1, 1970). For example, if 60 seconds have passed since epoch,T = 2.HMAC-SHA1– A cryptographic function that combines thesecretandTusing the SHA-1 hash algorithm.Truncate()– A function that shortens the final HMAC result into a readable numeric code (usually 6 or 8 digits).
The output code is valid for a short window of time (commonly 30 seconds), after which a new one is generated. Both the client and server must have their clocks reasonably in sync for this to work.
📱 Popular TOTP Apps
| App Name | Key Features |
|---|---|
| Google Authenticator | Free, simple, works offline; no cloud backup |
| Microsoft Authenticator | TOTP generation plus push-based 2FA; works with Microsoft services |
| Authy | Secure cloud backup, multi-device sync, encrypted storage |
| Aegis Authenticator | Open-source, biometric app lock, local encrypted backup (Android only) |
| 1Password / Bitwarden | Password managers that include TOTP generation for stored accounts |
💡 Tip: For extra security, choose apps that allow encrypted local backups or multi-device sync with biometric locks.
🔒 Advantages of TOTP
- 🛑 Offline Security: Codes are generated locally on the user’s device, requiring no network or SMS connection.
- 🔐 SIM-Swap Resistant: TOTP codes are not tied to your phone number, so attackers can’t hijack them via SIM swapping.
- 🧩 Platform Support: Most modern services support TOTP as part of their two-factor authentication system.
- 🆓 Free and Open: Many TOTP solutions are free and based on open standards.
⚠️ Limitations
| Limitation | Explanation |
|---|---|
| Phishing Risk | Users may still enter TOTP codes into fake websites if tricked. |
| No Push Notifications | Unlike Duo or Microsoft push-based 2FA, TOTP doesn’t notify you of logins. |
| Clock Dependency | Requires your phone and the server to be time-synchronized. |
| Device Loss Risk | If you lose your phone without backup codes, you may be locked out. |
🧩 Related Terms and Explanations
| Term | Explanation |
|---|---|
| 2FA (Two-Factor Authentication) | Security method requiring two types of verification: something you know (e.g., password) and something you have (e.g., TOTP code). |
| TOTP | A one-time password generated based on the current time and a secret key. |
| HOTP | Counter-based version of TOTP; the code changes after each login attempt. |
| HMAC (Hash-Based Message Authentication Code) | A cryptographic method that combines a key with a message using a hash algorithm to produce a tamper-resistant code. |
| RFC 6238 | The official technical document defining how TOTP works. |
| Authenticator App | A mobile application (like Authy or Google Authenticator) that generates TOTP codes. |
| Secret Key | The private key shared between the user and the service, used to generate codes. |
| Unix Epoch | The starting point for time in Unix systems — January 1, 1970, 00:00:00 UTC. |
| Time Drift | A mismatch between device and server clocks, which can cause TOTP to fail. |
| Truncate Function | A function that shortens the cryptographic output into a 6-digit code. |